The air in the SOC is thick with the hum of cooling fans and the stale scent of yesterday's coffee. Somewhere in the ether, a system is whispering secrets, and it’s our job to listen. Not with passive ears, but with an active, probing presence. Today, we’re not just scanning ports; we’re dissecting an adversary’s digital footprint before they even know they’re being watched. We’re talking about Nmap. Forget the basic port scan; we're going deep, treating every subnet like a crime scene and Nmap as our forensic toolkit.
Nmap, the Network Mapper, has been the bedrock of network discovery and security auditing for decades. It's the swiss-army knife that every operator, from the lone bug bounty hunter to the seasoned incident responder, keeps oiled and ready. But its true power lies not in the default commands, but in the nuanced application of its extensive scripting engine and advanced scanning techniques. This isn't about finding open ports; it's about understanding the *context* of those open ports, the services they run, and the vulnerabilities they might expose. It’s about shifting from a defensive posture to an offensive mindset, proactive and precise.
Table of Contents
- Understanding Nmap Fundamentals: Beyond the Basics
- Advanced Scanning Techniques: The Operator's Edge
- Leveraging the Nmap Scripting Engine (NSE)
- Real-World Application: A Walkthrough
- Engineer's Verdict: Is Nmap Still King?
- Operator's Arsenal
- Frequently Asked Questions
- The Contract: Securing the Perimeter
For those just dipping their toes into the vast ocean of cybersecurity, the temptation is to stick to the shallow end, to run `nmap -sV
Understanding Nmap Fundamentals: Beyond the Basics
Before we unleash the full might of Nmap, let's re-establish the baseline. You know about port scanning, likely the TCP SYN scan (`-sS`) which is stealthy and efficient, or the TCP Connect scan (`-sT`) which is reliable but noisier. But do you understand the nuances? The difference between a closed port, an open port, and a filtered port? That distinction is critical. A filtered port suggests a firewall is in play, a puzzle piece we need to account for in our attack plan.
Service version detection (`-sV`) is also a standard, but its accuracy depends on Nmap’s ability to probe the service effectively. And OS detection (`-O`)? It’s a guessing game based on TCP/IP stack fingerprinting. It’s good, but not infallible. Think of these as your initial reconnaissance sweeps. They tell you what's *visible*, but the real gold is in what's *hidden* or *misconfigured*.
"The goal isn't just to scan, it's to understand the landscape of the network, to map its defenses and its vulnerabilities with the precision of a cartographer charting unknown territories."
TCP SYN Scan (`-sS`)
This is the default and preferred scan type for privileged users. It works by sending a TCP SYN packet and waiting for a SYN/ACK (indicating an open port) or an RST (indicating a closed port). If no response is received or an ICMP "destination unreachable" error is returned, the port is considered filtered.
nmap -sS 192.168.1.0/24
TCP Connect Scan (`-sT`)
When SYN scan isn't possible (e.g., for unprivileged users), Nmap falls back to a full TCP connection. This is noisier as it completes the three-way handshake, leaving a trace in application logs.
nmap -sT 192.168.1.100
Service Version Detection (`-sV`)
This option attempts to determine the service protocol and version running on open ports. It sends a series of probes and analyzes the responses.
nmap -sS -sV 192.168.1.100
OS Detection (`-O`)
Nmap sends a series of crafted TCP, UDP, and ICMP packets to the target and analyzes the responses to guess the operating system. It requires at least one open and one closed TCP port to be found.
nmap -sS -O 192.168.1.100
Advanced Scanning Techniques: The Operator's Edge
Now, let's move past the fundamentals. Elite operators don't just identify open ports; they probe for specific vulnerabilities, enumerate configurations, and test for known exploits. This is where Nmap's advanced capabilities shine.
UDP Scanning (`-sU`)
UDP is stateless, making its scanning more challenging. Nmap sends UDP packets to ports and analyzes responses (or lack thereof). A "closed" status is reliable, but an "open|filtered" status is common, meaning Nmap can't definitively tell if the port is open or if a firewall is blocking the probe.
nmap -sS -sU -p 53,161,123 192.168.1.100
Scanning UDP is vital for enumerating services like DNS (port 53), SNMP (port 161), and NTP (port 123), which are often overlooked but can be a gateway into a network.
FIN, Null, and Xmas Scans (`-sF`, `-sN`, `-sX`)
These scans exploit RFC ambiguities in how different operating systems handle packets with specific flag combinations. They can be effective at bypassing simple packet filters and firewalls, especially on Windows systems which tend to ignore such packets, returning no response (indicating filtered or open).
nmap -sF 192.168.1.100
nmap -sN 192.168.1.100
nmap -sX 192.168.1.100
Remember, the effectiveness of these scans can vary greatly depending on the target OS and firewall configuration. Always test against a controlled environment first.
ACK Scan (`-sA`)
Primarily used to map firewall rulesets, the ACK scan determines whether ports are filtered or unfiltered. It doesn't determine if a port is open or closed, but rather if it’s reachable by an ACK packet. This is crucial for understanding firewall policies.
nmap -sA 192.168.1.0/24
Window Scan (`-sW`)
Similar to ACK scan, but it attempts to infer port state based on differences in the TCP window size field. This can sometimes reveal open ports when other scan types are blocked.
nmap -sW 192.168.1.100
Maimon Scan (`-sM`)
A less common scan that exploits a specific behavior of the old U.S. Robotics modem network (Maimon). It can sometimes identify open ports that other scans miss.
nmap -sM 192.168.1.100
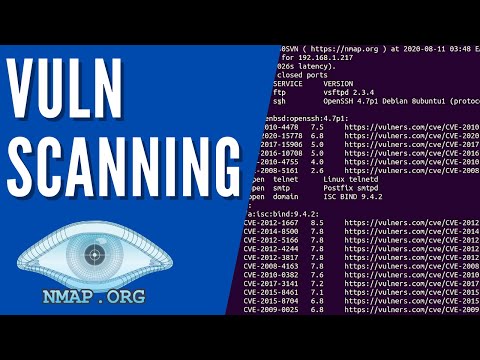
Leveraging the Nmap Scripting Engine (NSE)
Here's where Nmap transforms from a scanner into a vulnerability exploitation framework. The Nmap Scripting Engine (NSE) allows users to write and run scripts (in Lua) to automate a wide variety of networking tasks, including advanced detection, vulnerability discovery, and exploitation. This is the power-up that separates novices from seasoned professionals.
NSE scripts are categorized. Some are for discovery (`discovery`), others for vulnerability detection (`vuln`), brute-forcing (`brute`), default access (`default`), etc. When you think about a specific service or vulnerability, there's likely an NSE script for it. For example, `http-title` to grab web page titles, `smb-enum-shares` to find shares on Windows systems, or `ssl-heartbleed` to check for the Heartbleed vulnerability.
Running NSE Scripts
You can run specific scripts, categories of scripts, or even all scripts (`--script all`). However, running all scripts is time-consuming and can be intrusive. Targeted execution is key.
Running a specific script
nmap --script http-title <target-IP>
Running a category of scripts
nmap --script vuln <target-IP>
Running scripts based on discovered services
This is where it gets powerful. Nmap can automatically run scripts relevant to the services it detects.
nmap -sV --script default,discovery,safe <target-IP>
The `safe` category is designed to not crash services or exploit vulnerabilities, making it suitable for initial reconnaissance. When you need to go deeper, consider scripts from the `vuln` category, but always with caution and proper authorization.
Key NSE Scripts for Vulnerability Hunting:
http-enum: Enumerates common web application directories and files.smb-os-discovery: Discovers SMB details, including OS and domain.ssl-enum-ciphers: Enumerates SSL/TLS ciphers.ftp-anon: Checks for anonymous FTP login access.ssh-hostkey: Retrieves the SSH host key.mysql-info: Retrieves MySQL version and status.
This is just the tip of the iceberg. The `nmap --script help` command is your best friend, and the Nmap Scripting Engine documentation is a treasure trove. For any serious bug bounty hunter or penetration tester, mastering NSE is non-negotiable. It bridges the gap between basic port scanning and actionable vulnerability intelligence.
Real-World Application: A Walkthrough
Let's simulate a scenario. You've been tasked with auditing a small business network. You have a starting IP range: `192.168.5.0/24`. Your objective is to identify potential vulnerabilities that an attacker could exploit.
Phase 1: Initial Reconnaissance (Discovery & OS/Service Fingerprinting)
First, let's get a broad overview. We'll use a SYN scan for speed and stealth, enabling OS and version detection, and run some safe discovery scripts.
nmap -sS -sV -O -p- --script discovery,safe 192.168.5.0/24 -oN initial_scan.nmap
- `-sS`: TCP SYN scan (stealthy and fast).
- `-sV`: Service version detection.
- `-O`: OS detection.
- `-p-`: Scan all 65535 TCP ports.
- `--script discovery,safe`: Run scripts categorized as 'discovery' and 'safe'.
- `192.168.5.0/24`: The target subnet.
- `-oN initial_scan.nmap`: Save output to a file named `initial_scan.nmap`.
Reviewing `initial_scan.nmap`, you might find hosts with open ports like:
- Host `192.168.5.10` (likely gateway): Port 80 (HTTP), 443 (HTTPS) running Apache 2.4.x.
- Host `192.168.5.25`: Port 139, 445 (SMB) running Windows Server 2016.
- Host `192.168.5.50`: Port 3389 (RDP) open.
Phase 2: Targeted Vulnerability Scanning
Based on the initial scan, we can focus our efforts. Let's investigate the SMB service on `192.168.5.25` more deeply, and check the web server on `192.168.5.10` for common vulnerabilities.
Scanning SMB for vulnerabilities:
We'll use `smb-enum-shares` to find accessible shares and `smb-os-discovery` for more details. For suspected vulnerabilities, we might add `smb-vuln-*` scripts (use with extreme caution).
nmap -p 139,445 --script smb-enum-shares,smb-os-discovery,smb-vuln-ms17-010 192.168.5.25 -oN smb_scan_results.nmap
If `smb-vuln-ms17-010` reports a vulnerability, that's a critical finding. It indicates susceptibility to the WannaCry exploit.
Scanning the Web Server for vulnerabilities:
We'll check for common web application vulnerabilities and information disclosures.
nmap -p 80,443 --script http-enum,http-vuln-cve2017-5638,http-iis-webdav-scan 192.168.5.10 -oN web_scan_results.nmap
`http-enum` might reveal sensitive directories, while `http-vuln-cve2017-5638` checks for a specific Apache Struts vulnerability (example). Replace with relevant CVEs or vulnerability checks.
Phase 3: Aggressive Service Probing (Post-Exploitation Prep)
For critical hosts, especially those with RDP open or running older services, we might run a more comprehensive script scan. Here, we'll use the `vuln` category cautiously.
nmap -sV --script vuln 192.168.5.25 192.168.5.10 192.168.5.50 -oN vuln_scan.nmap
"Vulnerability scanning isn't about finding every flaw; it's about finding the *exploitable* flaws that provide the quickest path to compromise. Prioritize ruthlessly."
This walkthrough demonstrates how to move from broad network discovery to targeted vulnerability assessment using Nmap and its scripting engine. Each step builds upon the last, providing deeper insight and actionable intelligence.
Engineer's Verdict: Is Nmap Still King?
Nmap remains the undisputed king of network discovery and port scanning. Its flexibility, extensibility through NSE, and continuous development make it indispensable. However, it's not a silver bullet. For comprehensive vulnerability management, it needs to be part of a larger strategy. Dedicated vulnerability scanners (like Nessus, Qualys, or OpenVAS) offer more automated reporting and broader CVE coverage. But for the hands-on operator, the pentester, or the threat hunter who needs to understand the network's anatomy and probe for specific weak points, Nmap remains the foundational tool. Its power is directly proportional to the operator's skill and knowledge.
Operator's Arsenal
- Core Tool: Nmap (latest version)
- Scripting Language: Lua (for understanding NSE)
- Companion Scanners: Nessus Essentials (Free for home use), OpenVAS (Open Source), Qualys (Commercial)
- Exploitation Framework: Metasploit Framework (for PoC of found vulnerabilities)
- Traffic Analysis: Wireshark (for deep packet inspection)
- Key Reading: "Nmap Network Scanning" by Gordon "Fyodor" Lyon
- Certification (for formalizing skills): Offensive Security Certified Professional (OSCP) - demonstrates hands-on pentesting proficiency.
- Operating System: Kali Linux or Parrot Security OS (pre-loaded with Nmap and other security tools)
Frequently Asked Questions
Q1: Can Nmap directly exploit vulnerabilities?
Nmap's NSE scripts can automate the *detection* of many vulnerabilities and in some cases, perform proof-of-concept exploits. However, it is primarily a reconnaissance and vulnerability detection tool. For comprehensive exploitation, tools like Metasploit are generally more suited.
Q2: How can I make Nmap scans faster?
Use SYN scans (`-sS`), scan fewer ports (`-p
Q3: What's the most important NSE script category for a beginner?
Start with the `discovery` and `safe` categories. They provide valuable information without the risk of crashing services or triggering intrusion detection systems prematurely. Once comfortable, explore `default` and then cautiously move to `vuln` scripts for specific targets.
Q4: How do I deal with firewalls and IDS during Nmap scans?
Utilize slower timing (`-T0` to `-T2`), fragmented packets (`-f`), decoy IPs (`-D`), spoofed source IPs (`-S`), and scan for IDS evasion signatures (`--scan-delay`, `--max-parallelism`). Different scan types like FIN, Null, and Xmas scans can also bypass certain firewalls.
The Contract: Securing the Perimeter
Your mission, should you choose to accept it, is to conduct a comprehensive Nmap scan against a target environment of your choice (a lab setup is highly recommended). Document your findings. Identify at least three distinct hosts with potential vulnerabilities. For each identified vulnerability, provide the Nmap command used to detect it, the specific NSE script (if applicable), and a brief assessment of its potential impact. Then, outline the next steps you would take to confirm and potentially exploit this vulnerability. Show your work. The digital shadows are deep, and only the methodical survive.

No comments:
Post a Comment