The digital underbelly of the modern world is a shadowy place. In this realm, code isn't just instructions; it's a weapon. And the sharpest of these are known as payloads. These aren't abstract concepts discussed in sterile boardrooms; they are the instruments of intrusion, the keys that unlock doors you never knew existed. Today, we’re not just defining a payload; we’re dissecting it, understanding its lethal potential against a ubiquitous target: your Android device.
This isn't about fear-mongering; it's about illumination. In the cat-and-mouse game of cybersecurity, knowledge is the ultimate shield. Hackers wield payloads as their primary tool to gain unauthorized remote access. Understanding what they are, how they operate, and crucially, how to defend against them, is no longer optional—it's a prerequisite for survival in the connected age.
The cybersecurity landscape is littered with the digital debris of compromised systems. Often, the culprit is a well-crafted payload, designed to exploit vulnerabilities and grant attackers a clandestine foothold. This report delves into the anatomy of these digital infiltrators, with a specific focus on their deployment against Android devices—a platform that touches billions of lives daily. We'll explore the mechanisms of remote access, the techniques attackers employ, and most importantly, the proactive measures you can implement to bolster your defenses. The objective is clear: to arm you with the intelligence needed to navigate these threats and secure your digital presence.
Table of Contents
- What are Payloads?
- Payloads in Action: Android Exploitation
- Remote Access Vectors
- Staying Safe: Defensive Strategies
- Arsenal of the Analyst
- Frequently Asked Questions
- The Contract: Securing Your Digital Perimeter
What are Payloads?
At its core, a payload is the part of an attack code that performs malicious actions. Think of it as the "business end" of a cyberattack. When a vulnerability is discovered and exploited (often by an initial piece of code called the "shellcode" or "exploit"), the payload is what gets delivered to the target system to achieve the attacker's objectives. These objectives can range from stealing sensitive data, installing malware, creating a backdoor for persistent access, to completely taking over the compromised device.
In the context of cybersecurity, a payload is the malicious code or script that is executed on a target system after a vulnerability has been successfully exploited. It's the part that carries out the intended damage or grants the attacker the desired control. Without a payload, an exploit is merely a means to an end, unable to perform any action on its own.
Payloads can be incredibly varied in their design and function:
- Reverse Shell Payload: This is a classic. Instead of the attacker connecting to the compromised machine (a "bind shell"), the compromised machine initiates a connection back to the attacker. This is highly effective against systems behind firewalls.
- Meterpreter: A sophisticated payload from the Metasploit Framework, Meterpreter runs entirely in memory, leaving minimal traces on disk. It offers a wide range of functionalities, including file system manipulation, process control, and privilege escalation.
- Staged vs. Stageless Payloads: Stageless payloads contain all their necessary code in a single file, making them larger but simpler to deliver. Staged payloads are smaller and download their main components incrementally from the attacker's server, often for evasion purposes.
- Data Exfiltration Payloads: Designed specifically to identify, collect, and transmit sensitive data (credentials, financial information, intellectual property) back to the attacker.
- Ransomware Payloads: Encrypt files on the victim's system and demand payment for decryption.
The effectiveness of a payload often hinges on its stealth and its ability to bypass security mechanisms like antivirus software and intrusion detection systems. Attackers constantly refine their payloads to evade detection, making threat intelligence and up-to-date defenses paramount.
Payloads in Action: Android Exploitation
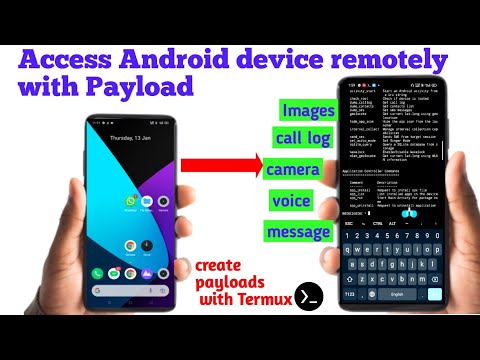
Android, with its open architecture and massive user base, presents a tempting target. Attackers leverage various vectors to deliver payloads to Android devices, aiming to gain remote control. The process typically involves tricking the user into executing a malicious application or exploiting a software vulnerability within the operating system or installed applications.
Imagine a digital detective, not solving a crime but perpetrating one. Their first step is finding a weakness, a crack in the armor. For Android, this often means exploiting vulnerabilities in the operating system, in third-party apps downloaded from unofficial sources, or even in common web browsers when users interact with malicious websites. Once a vulnerability is identified, the attacker crafts a payload designed to take advantage of it.
Here’s a simplified breakdown of how a payload might be delivered and executed on an Android device:
- Delivery: The payload is disguised as a legitimate application (e.g., a game, utility app, or even a seemingly harmless update). It might be distributed through unofficial app stores, phishing emails, malicious websites, or social engineering tactics.
- Execution: The user, unaware of the danger, installs and runs the malicious app. This execution triggers the payload.
- Privilege Escalation (Optional but Common): Many payloads seek to gain higher privileges on the device, moving from user-level access to system-level access. This allows for deeper control and access to more sensitive data.
- Command and Control (C2): The payload establishes a communication channel with the attacker's Command and Control server. This connection allows the attacker to send commands to the device and receive data in return.
- Malicious Action: The attacker, now with remote access, can perform various actions: steal contacts, SMS messages, call logs, location data, record audio/video, capture screenshots, install additional malware, or even wipe the device.
The notorious `Agent Tesla` or advanced Android RATs (Remote Access Trojans) are prime examples of sophisticated payloads designed for deep system compromise. They are stealthy, persistent, and can perform an alarming array of functions remotely.
Remote Access Vectors
Gaining remote access isn't magic; it's about exploiting communication channels and vulnerabilities. Attackers use a variety of methods to deliver and activate payloads on Android devices:
- Phishing and Social Engineering: Perhaps the most common vector. Attackers send emails, SMS messages (smishing), or social media messages containing links to malicious apps or websites. These messages are designed to trick users into downloading and installing the payload.
- Malicious Apps in Unofficial Stores: While Google Play Store has security measures, unofficial app marketplaces are often hotbeds for malware. Users seeking free paid apps or apps not available on the official store are at higher risk.
- Exploiting System Vulnerabilities: Although less common for typical users due to Android's security patching, zero-day or unpatched vulnerabilities in the Android OS or in widely used applications can be exploited remotely to deliver payloads without user interaction.
- Compromised Legitimate Apps: Sometimes, legitimate apps can be compromised through supply chain attacks, injecting malicious code into an otherwise trusted application.
- Watering Hole Attacks: Attackers compromise websites frequently visited by their target demographic. When a victim visits such a site, their device may be silently attacked, and the payload delivered.
The key takeaway is that remote access is rarely achieved through brute force; it's often a result of deception or the exploitation of overlooked weaknesses. The attacker's goal is to make the payload appear benign until it’s too late.
Staying Safe: Defensive Strategies
Protecting your Android device from malicious payloads requires a multi-layered approach. It's not about a single magical solution but a combination of good practices and vigilance. The digital world offers few guarantees, but disciplined habits significantly reduce your attack surface.
The street-smart approach to digital defense is simple: assume nothing is safe and verify everything. Attackers thrive on complacency. Here’s how to deny them that advantage:
- Install Apps Only from Trusted Sources: Stick to the Google Play Store. If you must venture elsewhere, thoroughly research the source and the app's reputation. Read reviews and check developer information.
- Review App Permissions Carefully: When installing or updating an app, scrutinize the permissions it requests. Does a flashlight app really need access to your contacts and SMS messages? If a permission seems excessive or unnecessary for the app's core function, do not grant it.
- Keep Your Android OS and Apps Updated: Manufacturers and app developers regularly release security patches to fix vulnerabilities exploited by payloads. Enable automatic updates wherever possible. Don't ignore those update notifications.
- Use a Reputable Mobile Security App: Antivirus and anti-malware software can detect and block known malicious payloads before they execute. Ensure it’s from a well-known vendor and keep its definitions updated.
- Be Wary of Links and Attachments: Treat links and attachments in emails, SMS, and social media with extreme skepticism. Hover over links to see where they lead before clicking. If a message seems suspicious, it probably is.
- Enable Two-Factor Authentication (2FA): While not directly preventing payload installation, 2FA adds a critical layer of security for your accounts, making it harder for attackers to leverage stolen credentials obtained via a payload.
- Disable Installation from Unknown Sources: In your Android settings, ensure that "Install unknown apps" is disabled for all applications, especially browsers and file managers. This is a critical preventative measure.
- Regular Backups: While not a preventative measure, having regular backups of your important data means that even if your device is compromised and data is lost or encrypted, you can restore it.
Your device is a gateway. Treat it with the respect it deserves, and it will serve you reliably. Neglect it, and you're inviting trouble.
Arsenal of the Analyst
For those delving deeper into understanding and defending against such threats, having the right tools is essential. While this post focuses on user-level protection, security professionals rely on a robust toolkit for analysis and defense.
- Metasploit Framework: An indispensable tool for penetration testers and security researchers, Metasploit provides a vast collection of exploits and payloads for testing system vulnerabilities. Understanding its capabilities is key to understanding attack methodologies. (Python, Ruby)
- Android Debug Bridge (ADB): Essential for interacting with Android devices from a computer. ADB allows for file transfers, installation of apps, running shell commands, and much more, making it invaluable for analysis and debugging.
- Wireshark: A powerful network protocol analyzer that allows you to capture and inspect traffic in real-time. This is crucial for analyzing how payloads communicate with C2 servers.
- Jupyter Notebooks: For data scientists and security analysts, Jupyter Notebooks provide an interactive environment for analyzing malware samples, network traffic logs, and threat intelligence data. Languages like Python are heavily used here.
- Mobile Security Framework (MobSF): An automated, all-in-one mobile application (Android/iOS) pen-testing, malware analysis, and security assessment framework capable of static and dynamic analysis.
- Books: "The Web Application Hacker's Handbook" (while focused on web, principles are transferable), "Android Internals: Revealing the Android System" for deep OS understanding.
- Certifications: While not a tool, certifications like OSCP (Offensive Security Certified Professional) or GIAC certifications in mobile security provide structured learning and validation of skills necessary to counter sophisticated threats.
Frequently Asked Questions
What is the difference between an exploit and a payload?
An exploit is the code or method used to take advantage of a vulnerability in a system. A payload is the malicious code that is *delivered* and *executed* by the exploit after the vulnerability is leveraged. The exploit opens the door; the payload walks through it and does the damage.
Can antivirus software always detect payloads?
No. While antivirus software is effective against known threats, attackers constantly create new, "polymorphic" or "metamorphic" payloads that evade signature-based detection. That's why behavioral analysis and user vigilance are also critical.
Is it possible for my phone to be infected without me installing anything?
Yes, though it's less common for average users. "Zero-day" vulnerabilities or sophisticated "drive-by" attacks on compromised websites can potentially deliver payloads without direct user interaction, but these typically target specific high-value individuals or large-scale campaigns.
What is the most common payload type for Android?
Currently, information-stealing malware and Remote Access Trojans (RATs) are some of the most prevalent payload types targeting Android, aiming to steal credentials, financial data, or gain ongoing control of the device.
How can I check if my Android device has a payload installed?
It can be difficult for the average user. Look for unusual battery drain, unexpected data usage, apps you don't recognize appearing, or your device behaving erratically. For a definitive answer, using a reputable mobile security scanner or consulting a professional is recommended.
The Contract: Securing Your Digital Perimeter
The threat of malicious payloads is a constant in the digital age. They are the silent saboteurs, the unseen agents of chaos, ready to exploit the slightest oversight. We've dissected their nature, understood their deployment against Android, and charted a course for defense. This knowledge isn't theoretical; it’s a tactical imperative. The contract is this: vigilance is your currency, and secure habits are your fortress.
Now, the real test. Imagine you discover a new application in an unofficial Android marketplace. It promises free access to a premium feature of a popular app. It has a few reviews, some positive, some vaguely concerning. What is your first analytical step before even considering installation, and what specific permission would immediately set off alarm bells if requested by this app?
```json
{
"@context": "https://schema.org",
"@type": "BlogPosting",
"headline": "Understanding Payloads: How They Can Remotely Access Android Devices and How to Stay Safe",
"image": {
"@type": "ImageObject",
"url": "https://example.com/images/payload-android-attack.jpg",
"description": "Illustration of a hacker's hand controlling an Android phone interface with malicious code visible."
},
"author": {
"@type": "Person",
"name": "cha0smagick"
},
"publisher": {
"@type": "Organization",
"name": "Sectemple",
"logo": {
"@type": "ImageObject",
"url": "https://example.com/images/sectemple-logo.png"
}
},
"datePublished": "2024-03-15T10:00:00+00:00",
"dateModified": "2024-03-15T10:00:00+00:00",
"mainEntityOfPage": {
"@type": "WebPage",
"@id": "https://www.sectemple.com/blog/understanding-android-payloads"
},
"description": "Learn about malicious payloads, how they grant remote access to Android devices, and crucial strategies to protect yourself from these cyber threats.",
"keywords": "payloads, android security, remote access, hacking, cybersecurity, malware, exploits, phishing, mobile security, threat intelligence"
}

