Table of Contents
- 0:00 - Introduction to Virtual Machines: The Deception and the Defense
- 2:26 - Importing a VM into VirtualBox: Establishing Your Sandbox
- 5:14 - Graceful Shutdown or Abrupt Halt? Stopping a VM
- 7:19 - Adapting the Interface: Resizing the VM's Display
- 9:59 - Command and Control: Keyboard Configuration of a VM
- 11:31 - Bridging Worlds: Networking Between Host and VM
- 16:01 - The Skeleton Key: VM Hardware Configuration
- 18:37 - Architecting the Web: Setting Up APACHE2 in a VM
- 25:17 - Deploying the Facade: Serving a Website with VM APACHE2
- 31:47 - Injecting Logic: Setting Up PHP in Your VM Environment
- 41:43 - Building the Backdoor: Creating a RESTful API Backend in a VM
Introduction to Virtual Machines: The Deception and the Defense
In the shadowy alleys of cyberspace, the concept of a virtual machine (VM) is both a marvel of engineering and a potential vector for compromise. At its core, a VM is the intricate virtualization or emulation of a computer system. These digital doppelgängers are built upon the foundational architectures of physical computers, providing a parallel functional space. Their implementation can range from the purely software-driven to intricate hardware-assisted constructs. Understanding VMs is paramount for any serious security professional. They are the sandboxes where we test our exploits, the isolated environments for analyzing malware, and, more critically, the potential vectors if not secured diligently.
Importing a VM into VirtualBox: Establishing Your Sandbox
The first step in dissecting any digital construct is to isolate it. VirtualBox, a popular hypervisor, serves as our initial containment unit. Importing a pre-configured virtual machine image, often found in OVA or OVF formats, is akin to unfurling a blueprint. This process establishes your discrete environment, a digital laboratory where operations can be conducted without jeopardizing the host system. However, remember: a sandbox is only as secure as its walls. Misconfigurations during import can leave the host vulnerable to the very threats you intend to study.
Graceful Shutdown or Abrupt Halt? Stopping a VM
Every controlled operation must have a controlled exit. Stopping a VM isn't merely flicking a switch; it's about managing the state of a running system. A graceful shutdown ensures that all processes terminate cleanly, data is saved, and the operating system within the VM enters a stable state. An abrupt halt, conversely, is the digital equivalent of yanking the power cord. This can lead to data corruption, file system inconsistencies, and potentially leave the VM in an unstable or unrecoverable state. For forensic analysis, the method of shutdown is as critical as the data itself.
Adapting the Interface: Resizing the VM's Display
The user interface of a VM, often rendered within a window on the host, may require adjustment. Resizing the display is a fundamental aspect of usability, allowing for better visibility and interaction. However, beyond mere aesthetics, the method used to achieve this (e.g., through guest additions or manual configuration) can reveal details about the VM's integration with the host and potential avenues for display-related exploits if not handled correctly.
Command and Control: Keyboard Configuration of a VM
Input is the conduit for command. The keyboard configuration of a VM dictates how your physical keystrokes are translated into digital actions within the virtual environment. This includes handling special key combinations, language layouts, and potentially preventing keyloggers from capturing sensitive data intended for the host rather than the VM—a crucial distinction in secure operations.
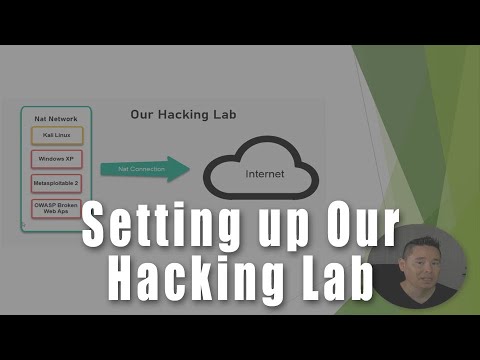
Bridging Worlds: Networking Between Host and VM
This is where the walls of the sandbox can become permeable. The network configuration between a host and its VM is a critical security consideration. Whether you opt for bridged mode, NAT, or host-only networking, each configuration presents a unique attack surface. Bridged mode can expose the VM directly to the network, while NAT provides a layer of obfuscation. Host-only networking, often the most secure for isolated analysis, limits communication solely to the host. Understanding these configurations is key to controlling the flow of data and preventing lateral movement by malicious actors.
The Skeleton Key: VM Hardware Configuration
Beneath the software veneer, a VM is a construct of virtualized hardware: CPU, RAM, storage, and network interfaces. Modifying these parameters—allocating more RAM, assigning more CPU cores, or emulating specific hardware—directly impacts performance and, crucially, the VM's compatibility with certain software or exploits. Over-allocating resources can starve the host system, while under-allocating can cripple the VM's functionality, potentially impacting the accuracy of your tests.
Architecting the Web: Setting Up APACHE2 in a VM
Serving web content from within a VM is a common practice for testing web applications and their underlying infrastructure. Apache HTTP Server (APACHE2) is a venerable workhorse in this domain. Its installation and configuration within a virtualized environment form the bedrock of many web-based security assessments. This involves not just the installation package but also understanding configuration files, virtual hosts, and access controls—all within the isolated context of the VM.
Deploying the Facade: Serving a Website with VM APACHE2
Once APACHE2 is installed, the next step is to deploy a website. This can range from a simple HTML static page to a dynamic application. For security professionals, this step is vital for replicating realistic web server environments, testing firewall rules, and understanding how web servers respond to various network inputs and requests before they hit production. The way APACHE2 is configured to serve content directly tells a story about the security posture of the VM.
Injecting Logic: Setting Up PHP in Your VM Environment
Many modern websites and web applications rely on server-side scripting languages like PHP. Integrating PHP with APACHE2 within the VM allows for the execution of dynamic content and the development of complex applications. This setup is crucial for penetration testers looking to probe for vulnerabilities in PHP code, such as insecure deserialization, command injection, or cross-site scripting (XSS) flaws that can be triggered through server-side logic.
Building the Backdoor: Creating a RESTful API Backend in a VM
The modern web is increasingly driven by APIs. Creating a RESTful API backend within a VM is a common task for developers and testers alike. For those on the defensive side, understanding API architecture, authentication mechanisms (like OAuth or JWT), and common vulnerabilities (like insecure direct object references or broken access control) is paramount. When setting up an API, you are essentially building a new entry point into your system—one that must be secured with military-grade precision.
Veredicto del Ingeniero: VMs as Tools of Insight
Virtual machines are indispensable tools in the cybersecurity arsenal. They provide isolated sandboxes for malware analysis, safe environments for testing exploits, and realistic staging grounds for web applications. As a defender, understanding their configuration, networking, and the software deployed within them is a non-negotiable skill. However, the allure of isolation can be deceptive. A poorly configured VM, especially one exposed to external networks, can quickly become a compromised node, granting attackers a foothold into your infrastructure. Treat every VM as a potential breach waiting to happen, and secure it accordingly.
Arsenal del Operador/Analista
- Hypervisors: VirtualBox, VMware Workstation/Fusion, KVM
- Security Tools: Wireshark, Metasploit Framework, Burp Suite
- Operating Systems: Kali Linux, Ubuntu Server, Windows Server Core
- Web Server Software: APACHE2, NGINX
- Scripting Languages: Python, PHP, Bash
- Key Books: "The Web Application Hacker's Handbook," "Practical Malware Analysis"
- Certifications: CompTIA Security+, OSCP (Offensive Security Certified Professional)
Taller Práctico: Fortaleciendo la Red de tu VM
-
Objetivo: Aislar la VM de la red externa para análisis seguro.
Acción: Configura la interfaz de red de tu VM en VirtualBox a 'Host-only Adapter'. - Verificación: Accede a la configuración de red de tu sistema operativo host para confirmar que solo ve la interfaz de red virtual específica para la comunicación host-VM.
- Refuerzo: Dentro de la VM, verifica la configuración de red (`ip addr` en Linux, `ipconfig` en Windows) y asegúrate de que solo tiene una dirección IP dentro del rango de la red 'Host-only'.
- Prueba de Aislamiento: Intenta realizar una conexión a Internet desde la VM. Si está configurada correctamente en modo 'Host-only', esta conexión debería fallar.
Preguntas Frecuentes
¿Qué es la principal diferencia entre una máquina virtual y un contenedor? Las máquinas virtuales emulan hardware y ejecutan un sistema operativo completo, mientras que los contenedores virtualizan a nivel del sistema operativo, compartiendo el kernel del host. Las VMs son más pesadas pero ofrecen mayor aislamiento.
¿Son las máquinas virtuales seguras para el análisis de malware? Sí, siempre y cuando se configuren de forma aislada (ej. modo 'Host-only' o red deshabilitada) y se tomen precauciones para evitar la fuga de infección al host. La configuración es clave.
¿Puedo ejecutar un sistema operativo diferente en una VM que en mi host? Absolutamente. Una de las grandes ventajas de las VMs es la capacidad de ejecutar sistemas operativos diversos (Linux en un host Windows, macOS en un host Linux, etc.) independientemente del sistema operativo anfitrión.
El Contrato: Asegura tu Entorno de Prueba
La verdadera maestría en ciberseguridad no reside solo en saber cómo romper sistemas, sino en cómo construir y mantener sus defensas inexpugnables. Has explorado la arquitectura de las máquinas virtuales, desde su creación hasta la implementación de servicios web. Ahora, el desafío es aplicar este conocimiento para fortificar tu entorno de laboratorio.
Tu Misión:
- Selecciona una VM (puedes usar una recién instalada o una que hayas configurado previamente).
- Implementa APACHE2 y sirve una página HTML estática simple.
- Antes de continuar, realiza una auditoría de red básica para esta VM. ¿Qué puertos están abiertos? ¿Qué información se revela en el banner del servidor?
- Configura la red de la VM en modo 'Host-only' para aislarla de la red exterior.
- Verifica que la conexión a Internet desde la VM está completamente deshabilitada.
Documenta tus hallazgos y las configuraciones aplicadas. Comparte tus resultados y cualquier técnica adicional que hayas empleado para aumentar la seguridad de tu VM en los comentarios. Recuerda, la seguridad es un proceso continuo de aprendizaje y adaptación.