The digital shadows lengthen as another week unfolds, bringing with it whispers of new threats and the ever-present debate around the laws that govern our digital frontier. Today, we dissect the lingering specter of Snake Keylogger found lurking within PDFs, the unsettling ease with which Teslas might be compromised via BLE, and the perennial question: does the updated Computer Fraud and Abuse Act (CFAA) truly offer sanctuary for those who operate in the grey areas of ethical hacking? This isn't just news; it's an intelligence briefing.
We'll be peeling back the layers of these stories, not to celebrate the breach, but to understand the anatomy of the attack and, more importantly, to fortify the defenses. Because in this game, knowing the enemy's playbook is the first step to building an impenetrable fortress.
Table of Contents
The Silent Invasion: Snake Keylogger in PDFs
The Vector is often the most innocuous: a seemingly legitimate PDF document. Yet, within its seemingly static structure, a malicious payload can lie dormant, ready to spring to life. Snake Keylogger, a notorious piece of malware, has resurfaced, embedding itself within these common file types. Its objective? To turn your digital interactions into a raw data feed for attackers. By exploiting vulnerabilities in PDF readers or employing social engineering tactics to trick users into enabling macros or scripts, Snake Keylogger gains a foothold. Once executed, it meticulously records keystrokes – login credentials, sensitive communications, financial details – transmitting them stealthily to command-and-control servers. This highlights a critical defensive posture: robust endpoint security, user education on identifying phishing vectors, and strict application hardening.
From a threat hunting perspective, detecting such activity requires vigilant monitoring of network egress traffic for unusual connections and payload delivery mechanisms. Analyzing PDF metadata and internal object structures for anomalies can also reveal a hidden threat before it's executed.
"The weakest link in security is almost always human. Train your users, or pay the price." - cha0smagick
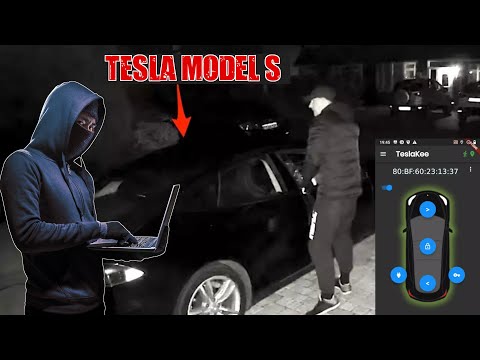
When Luxury Meets Vulnerability: Hacking Teslas via BLE
The allure of cutting-edge automotive technology often comes with an unforeseen shadow: the potential for exploitation. Recent findings indicate that Tesla vehicles, despite their sophisticated systems, are susceptible to attacks leveraging Bluetooth Low Energy (BLE). This vulnerability can potentially allow attackers to unlock doors, start the car, and even gain control over critical functions. The attack vector involves manipulating or spoofing BLE signals, effectively impersonating a legitimate key fob. This scenario underscores the importance of securing not just the digital infrastructure, but also the physical interfaces and wireless communication protocols that underpin modern devices.
Defensively, this necessitates understanding the BLE protocol's security primitives and how they can be circumvented. Implementing robust authentication mechanisms, employing encryption, and monitoring BLE traffic for unauthorized pairing attempts or unusual signal propagation are crucial steps. For manufacturers, it means a continuous cycle of security audits and secure development practices, assuming that every protocol has potential weaknesses.
The CFAA Conundrum: A Shield or a Smokescreen for Ethical Hackers?
The Computer Fraud and Abuse Act (CFAA) has long been a contentious piece of legislation in the cybersecurity landscape. For years, ethical hackers and security researchers have operated in a legal grey area, their actions often bordering on what the CFAA prohibits, even when performed with the best intentions. The Act, designed to prosecute malicious actors, has historically been criticized for its broad scope, which could inadvertently ensnare legitimate security professionals conducting vulnerability assessments or bug bounty hunting.
Recent discussions and potential policy updates aim to clarify the CFAA's application, seeking to provide better legal protection for ethical hacking activities. However, the devil is in the details. Will these updates offer a genuine shield, clearly defining the boundaries of permissible security research, or will they remain a smokescreen, leaving ethical hackers vulnerable to prosecution based on interpretation and intent? The core issue remains: how do we prosecute malicious intent without stifling beneficial security research?
From a defender's standpoint, understanding the legal frameworks surrounding security operations is as vital as understanding the technical exploits. It dictates the boundaries of penetration testing engagements and bug bounty programs. Clarity in these laws fosters a more transparent and collaborative security ecosystem.
The Genesis of ThreatWire: Context and Mission
ThreatWire, as a weekly news journalism show, aims to demystify the complex world of cybersecurity for a broad audience, from network administrators and information security professionals to the everyday consumer. Hosted by Shannon Morse, it serves as a crucial platform for disseminating timely information on security and privacy, translating technical jargon into understandable insights. The show's mission is to empower individuals with the knowledge needed to navigate the digital landscape safely and to foster a community informed about the evolving threat landscape.
This intelligence briefing is a product of that mission: to analyze, inform, and ultimately, to educate. The original publication date of May 24, 2022, serves as a temporal anchor, but the underlying principles and vulnerabilities discussed remain relevant. The inclusion of links to merchandise, Patreon, and social media reflects a common strategy for content creators to build a sustainable model around their educational efforts.
Arsenal of the Analyst
To effectively navigate the threats discussed, an analyst's toolkit is paramount. While this post focuses on news and legal aspects, the underlying technical challenges require specific tools:
- PDF Analysis Tools: Tools like
peepdf or origami can help dissect PDF structures, identify embedded scripts, and reveal potential malicious code.
- BLE Exploitation Frameworks: For understanding and testing BLE vulnerabilities, frameworks like
GATTTool (part of bluez) or specialized hardware with firmware like the Ubertooth One or HackRF are invaluable.
- Network Traffic Analyzers: Wireshark or tcpdump are essential for capturing and analyzing network packets, including BLE advertisements and connections.
- Legal Resources: Staying updated on cybersecurity law requires access to official legislative texts, DOJ advisories, and analyses from reputable legal scholars and cybersecurity think tanks.
- Bug Bounty Platforms: Platforms like HackerOne, Bugcrowd, and Synack are where many ethical hackers legally test systems, often operating under clear rules of engagement that align with their skills and the CFAA's intent.
Investing in these tools and platforms is not an expense; it's a strategic decision for any organization serious about its security posture or any individual aiming to build a career in information security. For those looking to formalize their knowledge, certifications such as the OSCP (Offensive Security Certified Professional) for offensive skills, or the CISSP (Certified Information Systems Security Professional) for a broader security management perspective, are highly recommended.
Frequently Asked Questions
What is Snake Keylogger and how does it spread?
Snake Keylogger is a type of malware designed to steal information by recording keystrokes. It is often distributed through malicious email attachments, phishing websites, or by embedding it within seemingly harmless documents like PDFs.
How can Teslas be vulnerable to BLE attacks?
Teslas, like many modern vehicles, use Bluetooth Low Energy (BLE) for keyless entry and ignition. Vulnerabilities can arise if the BLE signal can be intercepted, amplified, or spoofed, allowing an attacker to impersonate a legitimate key fob and gain unauthorized access.
Does the CFAA protect ethical hackers?
The CFAA's application to ethical hacking has historically been ambiguous and has led to concerns within the cybersecurity community. While recent efforts aim to clarify protections, the extent to which it shields legitimate security research is still subject to interpretation and ongoing legal developments.
Engineer's Verdict: Navigating Legal and Technical Minefields
The convergence of sophisticated technical vulnerabilities and evolving legal frameworks presents a complex challenge. On the technical side, the Tesla BLE vulnerability is a stark reminder that connectivity, while convenient, introduces attack surfaces that must be meticulously secured. Manufacturers must prioritize security from the design phase, not as an afterthought. For end-users, vigilance against social engineering and understanding the limitations of wireless security are critical defensive measures.
On the legal front, the CFAA situation is a tightrope walk. While the intent may be to protect cybersecurity professionals, the broad wording of such laws can still create a chilling effect. Ethical hackers must operate with extreme caution, adhering strictly to engagement scopes, obtaining explicit authorization, and maintaining detailed documentation of their activities. The best defense here is not just technical prowess, but impeccable legal compliance and a clear understanding of the boundaries. This is why formalizing your understanding through resources like comprehensive bug bounty program terms of service and legal counsel is advisable for serious practitioners.
The Contract: Fortifying Your Exploit Detection Capabilities
Consider this your initiation. The threats—Snake Keylogger, Tesla BLE exploits, legal ambiguities—are real. Your mission, should you choose to accept it, is to enhance your ability to detect and report such anomalies ethically and effectively.
Your Challenge:
- Simulate PDF Threat Detection: Using a safe, isolated lab environment, research tools or techniques for static analysis of PDF files to identify embedded scripts or suspicious objects. Document your findings in a hypothetical incident report template. You can practice this using sandboxed analysis tools and publicly available (non-malicious) PDF analysis examples.
- BLE Security Research Awareness: Research existing CVEs related to Bluetooth Low Energy security. Summarize one vulnerability and propose a hypothetical mitigation strategy that a vehicle manufacturer could implement.
- CFAA Interpretation Exercise: Find a recent news article or legal commentary on the CFAA and ethical hacking. Write a short (200-word) analysis from the perspective of a security consultant advising a client on the legal risks of unauthorized security testing.
The network is vast, and the threats are relentless. Your ability to dissect these challenges, both technically and legally, is what separates the novice from the true guardian of the digital realm. Report your findings, refine your methods, and stay vigilant.
What are your thoughts on the CFAA's impact on bug bounty hunters? Share your insights and experiences in the comments below. Let's debate.