La red es un campo de batalla de información. Cada búsqueda, cada clic, deja una huella. Y en el corazón de esta metrópolis digital, Google Ads se alza no solo como una plataforma publicitaria, sino como un vasto repositorio de intención humana. Ignorarla es como dejar el perímetro abierto en medio de la noche. Hoy, no vamos a 'hacer' investigación de palabras clave; vamos a diseccionar la herramienta para extraer inteligencia valiosa, aprendiendo a leer entre las líneas de los volúmenes de búsqueda y la competencia para anticipar movimientos y fortalecer nuestras defensas digitales.
Piensa en esto: ¿cómo reaccionarías si supieras exactamente qué está buscando tu adversario antes de que él mismo lo sepa? Esa es la esencia de la inteligencia de amenazas, aplicada al marketing de guerrilla digital. Google Ads, a pesar de su fachada comercial, es un polígono de tiro para entender las demandas latentes y explícitas del mercado. Dominar su "Keyword Planner" es tener una brújula en un océano de datos.
Tabla de Contenidos
- Paso 1: El Punto de Acceso - La Herramienta de Planificación de Palabras Clave
- Paso 2: Sembrando la Semilla de la Intención
- Paso 3: Desenterrando el Tesoro de las Palabras Clave
- Paso 4: Refinando la Señal - Filtrado Estratégico
- Paso 5: El Veredicto del Analista - Interpretación de Datos
- Arsenal del Operador/Analista
- Preguntas Frecuentes
- El Contrato: Tu Primer Análisis de Inteligencia de Mercado
Paso 1: El Punto de Acceso - La Herramienta de Planificación de Palabras Clave
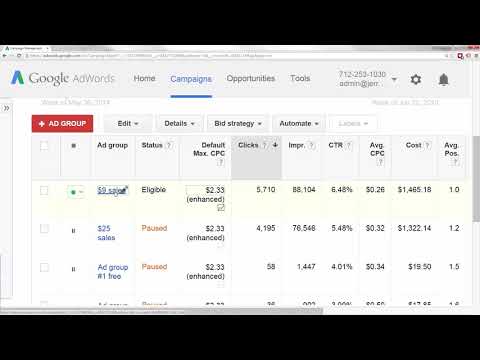
Para cualquier operación de inteligencia, necesitas acceso al sistema. En este caso, nuestro sistema es Google Ads. Si no tienes una cuenta, créala. Es un proceso estandarizado, pero recuerda, el objetivo aquí no es lanzar campañas, sino acceder a la sala de control de datos. Una vez dentro, navega hasta "Herramientas y configuración" y busca la "Planificación de palabras clave". Este es tu portal de entrada.
Este módulo, aunque diseñado para anunciantes, es un verdadero observatorio de la intención del usuario. Ignora las guías que te dicen cómo gastar dinero; concéntrate en la información que te proporciona sobre lo que la gente está escribiendo en ese mismo instante.
Paso 2: Sembrando la Semilla de la Intención
Aquí es donde mapeamos el terreno. Tienes una idea de lo que ofreces, de los servicios que proteges o de los mercados que analizas. Transforma esas ideas en consultas iniciales. Piensa como un atacante buscando un vector: ¿cuáles son las palabras, las frases, las combinaciones de términos que alguien usaría para encontrar tu "zona de interés"?
Introduce estas ideas de forma metódica en la sección "Buscar nuevas palabras clave". No te limites a una sola. Crea una lista variada, cubriendo diferentes ángulos y niveles de especificidad. Cuanto más rica sea tu entrada inicial, más profundo será el pozo de información al que accedas.
Paso 3: Desenterrando el Tesoro de las Palabras Clave
Al pulsar "Obtener ideas", Google Ads actúa como tu equipo de reconocimiento. Te devolverá un despliegue de términos relacionados, categorizados y, lo más importante, cuantificados. Presta atención a las métricas clave: el volumen de búsqueda mensual y el nivel de competencia. Estos números no son meros datos; son indicadores de actividad, de interés y de saturación.
Un alto volumen de búsqueda en combinación con baja competencia es un botín. Indica demanda existente con menos contendientes. Por el contrario, alta competencia y bajo volumen puede sugerir un nicho muy específico, quizás con un alto valor por clic, algo que los traders de cripto entienden bien.
Paso 4: Refinando la Señal - Filtrado Estratégico
Los resultados brutos pueden ser abrumadores. Aquí es donde aplicas tu criterio de analista. Utiliza los filtros disponibles para aislar la información más relevante. ¿Buscas términos con un alcance mínimo garantizado? Filtra por volumen de búsqueda. ¿Quieres evitar mercados saturados para encontrar tu ventaja? Filtra por competencia.
Puedes ir más allá. Considera la intención implícita en las palabras clave. ¿Son términos transaccionales ("comprar micrófono USB"), informacionales ("cómo funciona un micrófono USB") o comerciales ("mejor micrófono USB para streaming")? Cada uno revela una etapa diferente en el ciclo de decisión del usuario.
Paso 5: El Veredicto del Analista - Interpretación de Datos
Los números son solo una parte de la ecuación. Tu tarea es interpretar lo que significan. Un alto volumen de búsqueda para "cómo hackear WiFi" no es solo una métrica; es una señal de interés público en un tema sensible, que puede ser explotado por estafadores o, desde nuestra perspectiva, mitigado con educación.
Utiliza la herramienta de vista previa de anuncios para simular cómo se verían estos términos en el campo de batalla de los resultados de búsqueda. ¿Qué tipo de mensajes se destacarían? ¿Qué ofertas competidoras estarían presentes? Esta simulación te da una visión de 360 grados del panorama.
Arsenal del Operador/Analista
Para operaciones de inteligencia de mercado y de seguridad que requieran análisis profundo, necesitarás herramientas que complementen la información de Google Ads:
- Google Ads Keyword Planner: La herramienta principal para este análisis.
- SEMrush/Ahrefs: Soluciones comerciales robustas para análisis de competidores, palabras clave y backlinks. Indispensables para una inteligencia de mercado de élite.
- Google Trends: Para entender la estacionalidad y el interés evolutivo de las palabras clave.
- Python con Bibliotecas como `requests` y `BeautifulSoup`: Para web scraping automatizado de resultados de búsqueda y análisis de datos a gran escala.
- Jupyter Notebooks: Entorno ideal para análisis de datos, visualización y experimentación con código.
- Libro recomendado: "Don't Make Me Think" de Steve Krug. Aunque centrado en usabilidad, sus principios sobre la claridad y la intención del usuario son transferibles al análisis de palabras clave.
- Certificación (para demostrar maestría): Considera cursos avanzados de SEO y marketing digital que enfaticen el análisis de datos. Buscadores como Coursera o Udemy ofrecen excelentes opciones, pero para autenticación, la OSCP tiene su propio prestigio en el ámbito técnico.
Preguntas Frecuentes
¿Es realmente gratis usar Google Ads Keyword Planner?
Sí, puedes acceder a las funcionalidades básicas sin gastar dinero, aunque tener una campaña activa puede ofrecer datos más granularizados.
¿Cuántas palabras clave debo introducir inicialmente?
Empieza con 5-10 términos centrales y expande desde ahí. La clave es la diversidad.
¿Qué hago si no encuentro palabras clave relevantes?
Amplía tu perspectiva. Piensa en sinónimos, términos relacionados, problemas que tu solución enfrenta y el lenguaje coloquial que la gente usa.
¿Cómo afecta el volumen de búsqueda a mi estrategia de seguridad?
Un alto volumen para términos maliciosos indica áreas de riesgo público y potencial para operaciones de desinformación o phishing. Para aspectos benignos, indica demanda de tus servicios.
El Contrato: Tu Primer Análisis de Inteligencia de Mercado
Has desmantelado la herramienta. Ahora, aplica lo aprendido. Elige un tema de interés para ti (ciberseguridad, trading de criptomonedas, desarrollo de software). Utiliza Google Ads Keyword Planner como tu primera fase de reconocimiento. Identifica 5 términos clave con alto volumen y baja competencia. Luego, investiga en Google Trends la evolución de esos términos en los últimos 12 meses. Documenta tus hallazgos: ¿qué te dicen estos datos sobre la demanda y la conversación en línea?
“El conocimiento es poder. El conocimiento aplicado es influencia. El conocimiento aplicado de forma estratégica es dominio.” - cha0smagick
Este ejercicio no es solo para optimizar un sitio web, es para entrenar tu mente analítica. La misma metodología que usas para encontrar palabras clave rentables puede ser adaptada para identificar vectores de ataque, puntos débiles en sistemas o tendencias en el mercado de criptoactivos. El verdadero valor reside en tu capacidad para extraer inteligencia accionable de cualquier fuente de datos.
Ahora es tu turno. ¿Qué nicho has analizado? ¿Qué joyas ocultas encontraste? Comparte tus hallazgos, tus estrategias y tus herramientas favoritas en los comentarios. Demuestra que la verdadera inteligencia no se compra, se desarrolla.