The faint hum of servers in a darkened data center. For some, it's a lullaby. For others, the prelude to chaos. Port 21, the gateway for FTP, has long been a notorious entry point. It's a classic, a relic from a time when security was an afterthought. We're not here to talk about 'making money online' through questionable means. We're here to dissect the anatomy of an FTP enumeration attack and forge defenses that hold. This isn't about exploiting; it's about understanding to protect.
FTP, the File Transfer Protocol, has been a staple for moving files across networks since the dawn of the internet. Its ubiquity, however, belies a security posture that, in many deployments, remains alarmingly fragile. Port 21, the command port, is more than just a listening socket; it's a beacon for those who seek to probe the defenses of your digital fortresses. Understanding its enumeration is not about finding vulnerabilities to exploit, but about anticipating the attacker's reconnaissance and building a robust shield.
Understanding the FTP Enumeration Attack Vector
FTP enumeration is the process by which an attacker gathers information about FTP services on a target system. The goal is to identify running FTP servers, understand their configurations, and, critically, discover potential credentials or vulnerabilities that can be leveraged for deeper access. Think of it as a digital lockpick artist casing a building, noting every door, window, and potential weak point before attempting entry.
The initial phase usually involves a port scan. Tools like Nmap are indispensable here, scanning a target IP address to identify open ports. When port 21 is found listening, it signals the presence of an FTP service. But simply knowing port 21 is open is just the first whisper in a storm of potential information disclosure.
Key Enumeration Techniques for FTP
- Banner Grabbing: Many FTP servers reveal their version and operating system information directly in their initial banner message. This seemingly innocuous detail can provide attackers with a wealth of knowledge about known vulnerabilities specific to that software version. A simple `nmap -sV -p 21
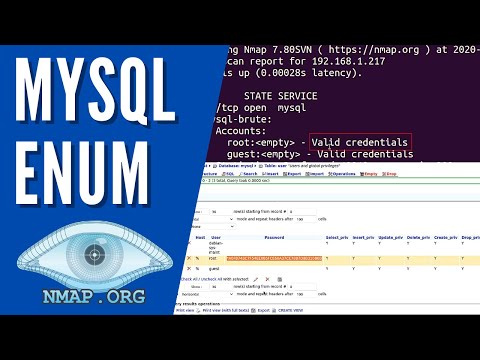
` can often reveal this. - Anonymous FTP Access: A significant number of FTP servers are configured to allow anonymous logins. Attackers will attempt to connect using common anonymous credentials like 'anonymous' or 'ftp' with any password. If successful, this grants access to publicly available files, which might contain sensitive information, configuration files, or even credentials for other services.
- Brute-Force and Dictionary Attacks: For servers requiring authenticated access, attackers will resort to brute-force methods. This involves systematically trying common usernames and passwords, often sourced from leaked credential databases or generated by dictionary lists. Tools like Hydra or Medusa are commonly employed for this purpose.
- Directory Traversal (via FTP Commands): Certain FTP clients and servers might have vulnerabilities that allow attackers to navigate directories beyond their intended scope using commands like `CWD` (Change Working Directory) or `CDUP` (Change Directory Up). This could expose sensitive configuration files or other restricted data.
- FTP Bounce Attack (PORT attack): A more advanced technique where the attacker uses a vulnerable FTP server to scan other internal or external ports. The attacker instructs the FTP server to connect to a specific IP and port, effectively using the server as a proxy to probe other services. This can be particularly dangerous if the FTP server resides within a restricted network segment.
These techniques, when combined, paint a comprehensive picture for an attacker. They move from simply identifying a service to understanding its configuration, potential user accounts, and pathways for deeper intrusion. For the defender, these are the very same signals we need to monitor.
Defending Against FTP Enumeration: The Blue Team's Arsenal
The narrative often focuses on the offensive. But true mastery lies in anticipating the enemy's moves and fortifying the perimeter. Defending against FTP enumeration isn't about a single magic bullet; it's a layered approach, a symphony of security controls.
Taller Práctico: Fortaleciendo tu Servidor FTP
- Disable Anonymous Access: If your FTP server does not require anonymous access, disable it entirely. This eliminates a common reconnaissance vector. Locate the `anonymous_enable` setting in your `vsftpd.conf` (or equivalent configuration file for your FTP server) and set it to `NO`.
- Enforce Strong Password Policies: Implement robust password policies for all FTP accounts. This includes minimum length, complexity requirements (uppercase, lowercase, numbers, symbols), and regular password rotation.
- Limit User Access with Chroot Jails: Configure your FTP server to 'chroot' users to their home directories. This prevents them from navigating outside their designated area, even if they manage to guess or acquire credentials. In `vsftpd.conf`, use `chroot_local_user=YES` and ensure `allow_writeable_chroot=YES` if users need write permissions within their chrooted environment (though be TREAD CAREFUL WITH THIS SETTING).
- Use SFTP or FTPS: Whenever possible, migrate away from plain FTP. SFTP (SSH File Transfer Protocol) runs over SSH (port 22) and provides encryption and authentication. FTPS (FTP over SSL/TLS) encrypts FTP traffic using SSL/TLS. Both offer significant security advantages over plain FTP.
- Network Segmentation and Firewalling: Restrict access to FTP servers to only necessary IP addresses or subnets. Implement strict firewall rules that only allow inbound connections on port 21 (or your chosen FTP port) from trusted sources. Block all other inbound traffic by default.
- Intrusion Detection/Prevention Systems (IDS/IPS): Deploy IDS/IPS solutions that can detect and potentially block suspicious FTP activity, such as an excessive number of login attempts, known malicious commands, or exploit attempts. Configure rules to monitor port 21 traffic for anomalies.
- Regular Auditing and Version Control: Periodically audit your FTP server configurations. Ensure you are running the latest, patched versions of your FTP server software. Vulnerabilities are discovered constantly, and staying updated is critical.
Guía de Detección: Monitorizando la Reconocimiento en Port 21
Detecting enumeration attempts is key to proactive defense. It's about spotting the probe before the breach.
- Analyze FTP Server Logs: Regularly review your FTP server logs (e.g., `vsftpd.log`). Look for patterns indicative of enumeration:
- A high volume of connection attempts from a single IP address.
- Repeated failed login attempts (brute-force).
- Successful anonymous logins that reveal unexpected file structures.
- Unusual command sequences (e.g., repeated `CWD` commands to probe directory structures).
- Monitor Network Traffic: Use network monitoring tools (e.g., tcpdump, Wireshark, or SIEM solutions) to capture and analyze traffic on port 21. Look for:
- Unusual packet sizes or frequencies.
- Connection attempts from known malicious IP addresses.
- Traffic patterns that deviate from normal user behavior.
- Implement Account Lockout Policies: Configure your FTP server or underlying OS to lock out accounts after a certain number of failed login attempts. This significantly hinders brute-force attacks.
- Honeypots: Consider deploying an FTP honeypot. This is a decoy server designed to attract attackers. Any traffic directed to the honeypot is, by definition, malicious and can provide valuable intelligence on attacker TTPs (Tactics, Techniques, and Procedures).
Veredicto del Ingeniero: ¿Vale la pena mantener FTP?
FTP, in its plain, unencrypted form, is largely a liability in modern security environments. Its enumeration is trivial, and its vulnerabilities are well-documented. If your organization still relies on plain FTP for sensitive data transfer, the question isn't if it will be compromised, but when.
Verdict: Strongly advise migration to SFTP or FTPS. If plain FTP must be maintained for legacy reasons, it should be heavily restricted by network firewalls, access controls, and vigilant logging. It's a critical weakness that attackers will always probe first.
Arsenal del Operador/Analista
- Nmap: Essential for port scanning and service version detection.
- Hydra / Medusa: For brute-force authentication attacks (use ethically in controlled environments).
- Wireshark / tcpdump: For deep packet inspection and network traffic analysis.
- vsftpd: A popular, secure FTP daemon (highly configurable for defense).
- SSH: The foundation for secure alternatives like SFTP.
- Books: "The Web Application Hacker's Handbook" (while web-focused, covers foundational principles), "Network Security Assessment" by Chris McNab.
- Certifications: CompTIA Security+, CEH (Certified Ethical Hacker), OSCP (Offensive Security Certified Professional) - understanding offense sharpens defense.
Ignoring the risks associated with FTP enumeration is not an option. It's a fundamental part of reconnaissance that can lead to significant breaches. By understanding these techniques and implementing proactive defensive measures, you can transform a potential liability into a secured gateway.
Preguntas Frecuentes
¿Puedo usar FTP de forma segura?
Plain FTP (port 21) is inherently insecure due to its lack of encryption. It is highly recommended to use SFTP (SSH File Transfer Protocol) or FTPS (FTP over SSL/TLS) for secure file transfers. These protocols encrypt credentials and data in transit.
¿Qué es el "FTP Bounce Attack"?
An FTP Bounce Attack (or PORT attack) exploits a vulnerability in FTP servers to make them act as a proxy. An attacker can command a vulnerable FTP server to establish a data connection to a third-party host and port, effectively using the FTP server to scan or attack other systems within a network it has access to.
¿Cuál es la diferencia entre SFTP y FTPS?
SFTP is a completely different protocol that runs over SSH (typically on port 22). It's designed for file transfer and uses SSH's encryption and authentication. FTPS is an extension of FTP that adds SSL/TLS encryption to the standard FTP protocol, often using ports 990 (implicit FTPS) or 21 (explicit FTPS). SFTP is generally considered more robust and easier to implement securely.
¿Cómo puedo proteger mi servidor FTP de ataques de fuerza bruta?
Implement account lockout policies, enforce strong password complexity, use SFTP or FTPS, restrict access via firewalls to known IP addresses, and monitor server logs for suspicious activity. Regularly update your FTP server software as well.
¿Qué información puede obtener un atacante mediante la enumeración de FTP?
An attacker can discover the FTP server's version and OS (revealing potential vulnerabilities), identify if anonymous access is allowed, find valid usernames and passwords through brute-force or leaked databases, and potentially uncover sensitive files if directory traversal is possible or anonymous access is misconfigured.
El Contrato: Asegura el Perímetro Digital
Now that you understand the subtle art of FTP enumeration and the crucial steps to fortify your defenses, the real work begins. Your challenge: conduct an audit of your own network. Identify any systems still running plain FTP. Document the risks, propose migration steps to SFTP/FTPS, and implement at least two of the defensive measures discussed in this guide on a test system. Report your findings. The digital realm doesn't forgive ignorance; it punishes it. Show me you're ready to defend.