The digital battlefield is an ever-shifting landscape. Email, once a simple communication tool, is now a primary vector for adversaries looking to breach the gates. In this relentless campaign, Microsoft Defender for Office 365 stands as a critical sentinel, offering insights into the shadows of your organization's communication channels. This isn't about casual browsing; it's about a methodical hunt, a forensic dissection of digital intrusions. If your organization is equipped with Defender for Office 365, you hold the keys to the kingdom's surveillance – the Explorer and Real-time Detections dashboards.
Forget the fairy tales of instant security. True defense is born from relentless investigation. We're not just looking at alerts; we're hunting anomalies, tracing the digital footsteps of attackers. This guide is your operational manual, detailing how to wield Defender for Office 365 not just as a shield, but as a scalpel for threat investigation.
Table of Contents
- Understanding the Battlefield: Explorer vs. Real-time Detections
- Setting the Trap: Proactive Notification Strategies
- Deep Dive: The Art of the Explorer Hunt
- Real-time Response: Leveraging Detections in the Heat of the Moment
- Forensic Analysis of Individual Email Messages
- Securing Collaboration Platforms: SharePoint & OneDrive Investigations
- Engineer's Verdict: Is Defender for Office 365 Your Knight in Shining Armor?
- Operator's Arsenal: Essential Tools for the Defender
- Defensive Workshop: Crafting High-Fidelity Detection Rules
- Frequently Asked Questions
- The Contract: Your First Simulated Threat Hunt
Understanding the Battlefield: Explorer vs. Real-time Detections
Defender for Office 365 presents two primary operational theaters: Explorer and Real-time detections. Explorer is your historical archive and deep-dive analysis tool. It allows you to sift through past events, trace the lifecycle of threats, and understand attack patterns over time. Think of it as a cold case unit for digital crimes. Real-time detections, conversely, is your live surveillance feed. It’s the immediate alarm system, flagging suspicious activities as they unfold. Mastering both is key to a robust defense. You'll find these powerful features under 'Threat management' within the Microsoft 365 Defender portal.
Setting the Trap: Proactive Notification Strategies
The attacker rarely announces their arrival. Your first line of defense is an early warning system. Configuring precise email notifications within Microsoft Defender for Office 365 is non-negotiable for any security team. This isn't about drowning in alerts; it's about ensuring critical events reach the right eyes without delay. Define alert policies that are tuned to your environment's specific risks. Too much noise, and you'll miss the critical signal. Too little, and you'll be blindsided.
Deep Dive: The Art of the Explorer Hunt
Explorer is where the true hunting begins. It’s not merely about viewing detected threats; it's about understanding their context. Use Explorer to dissect specific malicious campaigns, identify compromised endpoints, and track the spread of malware or phishing attempts. Query the data. Filter by sender, recipient, subject, threat type, and time range. Look for anomalies: unusual attachment types, suspicious sender domains, or a sudden spike in outbound phishing attempts. Each query is a probe into the enemy's strategy. Remember, the goal is to build a comprehensive picture, not just close an individual ticket.
Real-time Response: Leveraging Detections in the Heat of the Moment
When an alert fires from Real-time detections, speed is paramount. This feature provides an immediate snapshot of ongoing threats. Unlike Explorer's historical view, Real-time detections are your frontline intelligence. Use this to quickly cordon off compromised mailboxes, block malicious domains or sender addresses, and initiate incident response protocols. The objective here is rapid containment and eradication before the adversary can achieve their objectives.
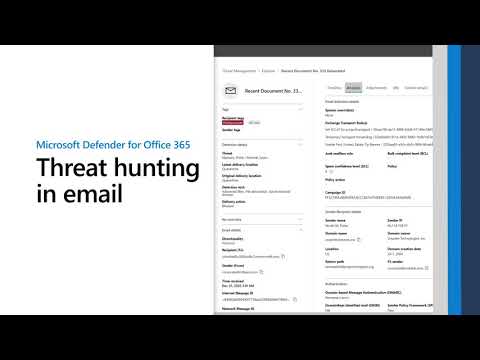
Forensic Analysis of Individual Email Messages
Sometimes, a user reports a suspicious email, or a gut feeling tells you something is off. Defender for Office 365 allows for granular inspection of individual messages. Dive into the full headers, analyze attachment metadata, and examine any embedded links. This level of detail is crucial for confirming a threat, understanding its payload, and gathering indicators of compromise (IoCs) that can be used to protect the rest of your infrastructure. Treat every suspicious email as a potential gateway – analyze it thoroughly.
Securing Collaboration Platforms: SharePoint & OneDrive Investigations
The threat landscape extends far beyond email. SharePoint and OneDrive for Business are fertile grounds for attackers seeking to exfiltrate data or host malicious payloads. Defender for Office 365 provides visibility into these environments. Investigate suspicious file sharing activities, unauthorized access attempts, or the presence of malware within document repositories. Understanding these vectors allows you to fortify your collaboration tools, ensuring sensitive data remains behind secure digital walls.
Engineer's Verdict: Is Defender for Office 365 Your Knight in Shining Armor?
Microsoft Defender for Office 365 is a formidable tool, especially for organizations already embedded in the Microsoft 365 ecosystem. Its strength lies in its integration and the depth of telemetry it provides specifically for email and collaboration threats. However, it's not a silver bullet. Its effectiveness is directly proportional to the skill and diligence of the operator. Without a proactive hunting mindset and a solid understanding of adversary tactics, even the most advanced tools can become mere alert generators. For organizations heavily reliant on Microsoft services, it’s an essential component of a layered defense strategy, but it requires skilled personnel to truly unlock its potential.
Operator's Arsenal: Essential Tools for the Defender
- Microsoft 365 Defender Portal: The central command for threat hunting and incident response.
- SIEM/SOAR Platforms (e.g., Splunk, Microsoft Sentinel): For correlating Defender for Office 365 logs with other security data and automating response actions.
- Threat Intelligence Feeds: To enrich your investigations with external context on known malicious actors and campaigns.
- Communication Tools (e.g., Slack Enterprise Grid, Microsoft Teams): To coordinate incident response efforts effectively.
- Documentation Tools (e.g., Confluence, OneNote): To record findings, IoCs, and remediation steps for future reference and training.
Defensive Workshop: Crafting High-Fidelity Detection Rules
Alerts are meaningless if they don't lead to action. The true value of Defender for Office 365 lies in tuning your detection capabilities. Let's consider a scenario: detecting credential harvesting attempts disguised as legitimate login prompts. Instead of relying solely on built-in alerts, you can craft custom detection rules.
Consider the following as a conceptual guide:
- Hypothesize: Attackers often use domain-spoofing techniques or redirect users to fake login pages. Look for emails with links pointing to external domains that mimic legitimate organizational URLs, especially those with slight misspellings or unusual TLDs, and originating from unexpected sender addresses.
- Data Collection: Leverage Explorer to query emails containing links to known credential harvesting domains or IPs. Filter by attachment types often used in phishing (e.g., .html, .zip).
- Analysis: Examine the headers of suspicious emails. Look for inconsistencies in the mail routing or discrepancies between the purported sender and the actual originating IP. Use Defender's message trace functionality to follow the path an email took to reach its destination.
-
Rule Creation (Conceptual KQL for Microsoft Sentinel/Defender):
// Conceptual rule to detect potential credential harvesting emails EmailEvents | where Timestamp > ago(7d) | where isnotempty(UrlInClutter) // Check if URLs were found | mv-expand UrlInClutter // Expand URL array | extend ParsedUrl = parse_url(UrlInClutter) | where ParsedUrl.Host startswith "login-" or ParsedUrl.Host endswith ".com" // Basic URL pattern matching | where ParsedUrl.Host !contains "yourcompany.com" // Exclude legitimate domains | where SenderFromAddress !contains "yourcompany.com" // Exclude internal senders | project Timestamp, Subject, SenderFromAddress, RecipientEmailAddress, UrlInClutter, ParsedUrl.Host | summarize count() by SenderFromAddress, RecipientEmailAddress, ParsedUrl.Host | where count_ > 2 // Potentially a campaign if multiple emails to a recipient from same sender/URL - Tuning & Response: Once a rule is in place, monitor its output. Tune it to reduce false positives. When triggered, initiate an incident response playbook: isolate the recipient's account, block the malicious URL, and conduct a broader hunt for similar threats.
Frequently Asked Questions
-
Q: What are the minimum permissions required to use Explorer and Real-time detections?
A: Typically, roles like Security Administrator, Security Operator, or Compliance Administrator grant the necessary permissions. -
Q: Can I export data from Defender for Office 365 for external analysis?
A: Yes, Microsoft 365 Defender allows for data export for further investigation, subject to your organization's data governance policies. -
Q: How often is the data in Explorer updated?
A: Data in Explorer is typically available within 30 minutes to a few hours, depending on the data source. Real-time detections are, as the name suggests, near real-time.
The Contract: Your First Simulated Threat Hunt
Your mission, should you choose to accept it: Within your organization's test environment or a controlled lab, simulate a phishing campaign targeting a test mailbox. Use Defender for Office 365's Explorer to track the phishing email, analyze its headers, and identify the malicious link or attachment. Then, use the threat hunting capabilities to search for any other instances of similar emails within your simulated environment. Document your findings, including IoCs and the steps taken to block or remediate the threat. This practical exercise solidifies the principles discussed and establishes your baseline for proactive defense.
In this digital theater, ignorance is not bliss; it's a vulnerability. Microsoft Defender for Office 365 offers a powerful suite of tools for the diligent threat hunter. By mastering its capabilities, you can move beyond reactive defense and adopt a posture of proactive vigilance, safeguarding your organization's most critical communication channels.

No comments:
Post a Comment