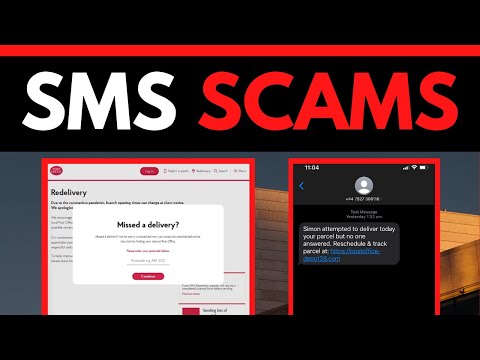
- **Generic Greeting**: "Your package" lacks personalization. Legitimate services usually address you by name or use a specific tracking number in the initial alert.
- **Urgency and Fear**: The implication of a failed delivery or a pending fee pressures immediate action.
- **Suspicious Link**: The URL itself is a primary indicator. It might be a slightly misspelled domain (typosquatting), a URL shortener designed to obfuscate the true destination, or a domain unrelated to legitimate postal services.
- **Request for Payment/Information**: Legitimate services rarely ask for payment or sensitive details directly via SMS link for standard deliveries.
- **Be Skeptical**: Treat all unsolicited messages with suspicion. If a message seems odd, it probably is.
- **Verify Independently**: Never click links or call numbers provided in suspicious messages. If an alert claims to be from your bank or a service you use, access your account through the official app or by typing the company's known web address directly into your browser.
- **Recognize Social Engineering Tactics**: Understand that attackers prey on emotions like fear, curiosity, and greed.
- **Guard Personal Information**: Never share passwords, PINs, Social Security numbers, or other sensitive data via text message.
- **Spam Filters**: Most smartphones have built-in spam filtering for messages. Ensure these are enabled and consider third-party apps that offer more robust filtering.
- **Block Unknown Senders**: Configure your phone to block messages from unrecognized numbers or those that exhibit spam-like characteristics.
- **Antivirus/Security Software**: Install reputable mobile security software. While not foolproof against phishing links, it can help detect malicious downloads or flag dangerous websites.
- **Operating System Updates**: Keep your mobile device's operating system and applications updated. Patches often fix security vulnerabilities that attackers exploit.
- **Security Awareness Training**: Regular, engaging training sessions are crucial. They should cover current phishing tactics, including smishing, and provide clear procedures for reporting suspicious communications.
- **Endpoint Security**: Deploy endpoint detection and response (EDR) solutions on all company devices. These can help detect and contain malware if a user succumbs to a smishing attempt.
- **Clear Reporting Channels**: Establish a straightforward process for employees to report suspicious messages or potential security incidents without fear of reprisal. This feedback is invaluable for threat intelligence.
- **Business Endpoint Testing**: If you're unsure about your organization's defenses, consider having them professionally tested. We offer comprehensive endpoint testing to identify weaknesses before attackers do: http://tpsc.tech/.
Arsenal del Operador/Analista
- Mobile Security Suites: Lookout, Norton Mobile Security, Avast Mobile Security.
- Password Managers: LastPass, 1Password, Bitwarden (for secure credential management).
- Reporting Resources: National Cybersecurity Alliance (USA), Action Fraud (UK), various national CERTs.
- Threat Intelligence Platforms: Tools for analyzing IoCs and attack patterns (specific tools vary by organizational needs).
- Business Continuity & Incident Response Planning: Crucial documentation for any organization.
Taller Práctico: Fortaleciendo tu Buzón contra Smishing
- Habilitar Filtro de Spam:
En iOS: Ve a Ajustes > Mensajes > Filtro de Mensajes Desconocidos.
En Android: Abre Mensajes > Menú (tres puntos) > Ajustes > Spam y Contactos Bloqueados > Habilitar Protección contra Spam.
- Revisar Reglas de Mensajes:
Verifica si tu aplicación de mensajería permite crear reglas personalizadas para filtrar mensajes sospechosos o por remitente.
- Configurar Bloqueo de Números:
Guarda números sospechosos que te molestan y bloquéalos. Si recibes un mensaje de un remitente recurrente de spam, bloquéalo directamente desde la conversación.
- Instalar Software de Seguridad:
Investiga y descarga una aplicación antivirus/antimalware de buena reputación desde la tienda oficial de tu sistema operativo. Asegúrate de que ofrezca protección web o contra phishing.
- Practicar la Verificación Independiente:
Ejercicio: Recibe un mensaje SMS que parezca sospechoso (ej: un banco indicando un problema). En lugar de hacer clic, busca el número de atención al cliente oficial de tu banco en su sitio web (buscando en Google, por ejemplo, "Nombre del Banco atencion cliente") y llama para verificar la alerta.
Preguntas Frecuentes
¿Por qué los ataques de smishing están aumentando?
Los atacantes se benefician de la alta penetración de smartphones y la confianza que la gente deposita en los mensajes de texto. Es un vector de ataque de bajo costo y alta efectividad contra el eslabón más débil: el factor humano.
¿Son efectivos los filtros de spam para SMS?
Sí, son una capa de defensa útil, pero no infalible. Los atacantes adaptan sus tácticas y los filtros a menudo se centran en patrones conocidos. La vigilancia personal es crucial.
¿Qué debo hacer si un enlace de smishing me pide instalar una aplicación?
NO LO HAGAS. Las solicitudes de instalación de aplicaciones a través de enlaces de SMS no solicitados son casi siempre maliciosas. Las aplicaciones legítimas se descargan de las tiendas oficiales (App Store, Google Play).
¿Cómo puedo denunciar un intento de smishing?
Puedes denunciar el mensaje a tu operador de telefonía móvil. En muchos países, existen agencias gubernamentales o de ciberseguridad (como el CERT/CSIRT nacional) donde se pueden reportar estos incidentes.
¿Es seguro hacer clic en enlaces acortados en SMS?
Los enlaces acortados son una herramienta común en smishing para ocultar la URL maliciosa real. Debes tratarlos con extrema precaución. Si no esperas el mensaje o el enlace, no hagas clic.
"Los humanos son la clave más débil en la cadena de seguridad. Se trata de ingeniería social, no solo de código." - Un operador anónimo de Sectemple.
"La seguridad no es un producto, es un proceso. Y la complacencia es el primer paso hacia la brecha." - cha0smagick.
El Contrato: Asegura Tu Buzón de Entrada
Ahora que has desmantelado la anatomía de un ataque de smishing y has fortalecido tus defensas, el desafío es mantener esta vigilancia. Tu contrato es simple: implementa al menos una de las estrategias de defensa técnica mencionadas hoy en tu dispositivo personal. ¿Es un filtro de spam más agresivo? ¿Una nueva aplicación de seguridad? ¿O te comprometes a verificar de forma independiente cada alerta inusual? Documenta tu elección y tu experiencia en los comentarios de abajo. Demuéstrame tu compromiso con la seguridad proactiva.
gemini_metadesc: Learn how to identify and defend against SMS phishing (smishing) attacks. This post dissects real-world examples and provides actionable prevention and recovery strategies for individuals and organizations. gemini_labels: smishing, SMS phishing, social engineering, cybersecurity awareness, threat hunting, incident response, mobile security, phishing prevention
No comments:
Post a Comment