The digital forensics lab is cold, sterile, illuminated by the flickering glow of terminals. Logs spill across screens like digital entrails, each line a potential clue, a whisper from the attacker. But not all whispers carry the same weight. Some are mere echoes, easily dismissed. Others are screams. This is where the Pyramid of Pain becomes our compass, a framework not to merely identify what an adversary left behind, but to strategically analyze and prioritize those fragments of evidence. We're not just collecting IOCs; we're dissecting the attacker's pain points.
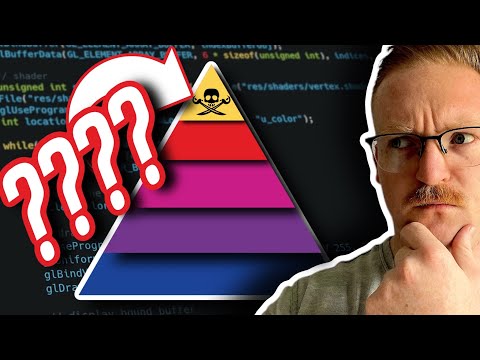
The Pyramid of Pain, conceived by the renowned David J. Bianco, offers a critical lens through which defenders can measure the efficacy of their detection and response strategies. It ranks Indicators of Compromise (IOCs) based on the difficulty an attacker would face in changing them. This difficulty directly correlates to the attacker's "pain" when these IOCs are detected and leveraged. Understanding this hierarchy is paramount for any organization aiming to move beyond reactive security towards a proactive, intelligence-driven defense posture.
The core principle is simple: the more difficult an IOC is for an attacker to alter, the more valuable it is for the defender. Conversely, easily mutable IOCs provide a fleeting advantage, as an attacker can swiftly adapt and bypass detection. Our mission isn't just to identify threats, but to identify the threats that will inflict the most strategic damage on an adversary's operations.
Table of Contents
- The Foundation: Hash Values
- The Next Level: IP Addresses
- Static Artifacts: Domain Names
- The Crucial Layer: Host Artifacts
- The Apex: Adversary Tactics, Techniques, and Procedures (TTPs)
- Leveraging the Pyramid: Strategic Threat Hunting
- Veredicto del Ingeniero: Embracing Pain for Gain
- Arsenal del Operador/Analista
- Preguntas Frecuentes
The Foundation: Hash Values
At the base of the pyramid lie hash values. These are the digital fingerprints of files – malware samples, configuration files, or scripts. When we identify a malicious file, we can calculate its hash (like MD5, SHA-1, or SHA-256). An attacker can easily generate a new executable with a different hash, evading simple signature-based detection methods.
"A signature is a fingerprint, and fingerprints can be smudged. We're looking for more than just smudges."
While essential for identifying known threats and crucial for malware analysis, relying solely on hashes is a tactical error. A simple recompilation or repacking can render a hash-based indicator useless. For defenders, this means that while tracking known malware hashes is necessary, it's a low-effort, high-churn activity for the adversary. The intelligence gained is transient.
The Next Level: IP Addresses
Moving up, we encounter IP addresses. These are the network addresses used by attackers to host command-and-control (C2) servers or launch attacks. Identifying malicious IP addresses can be highly effective in blocking incoming or outgoing malicious traffic. However, attackers can relatively easily spin up new IP addresses, use proxy services, or shift their infrastructure.
The pain inflicted is moderate because changing an IP address is a straightforward operational task for a determined adversary. While blocking known malicious IPs is a standard practice, it requires constant vigilance and threat intelligence feeds to remain effective. The lifespan of an IP-based IOC is often limited, demanding swift action.
From a defensive perspective, the value of IP addresses lies in their correlation with other behaviors. An IP address alone might be ephemeral, but an IP address exhibiting specific patterns of communication, hosting specific services, or associated with known malicious domains becomes a more robust indicator.
Static Artifacts: Domain Names
Domain names represent the next tier. Similar to IP addresses, attackers use domains for C2 infrastructure, phishing sites, or malware distribution. Registering new domain names is relatively easy and inexpensive. However, the process of establishing a reputable domain, building a brand around it, and configuring its associated infrastructure takes time and effort. This makes domain names slightly more painful for an attacker to change compared to IP addresses.
Detecting malicious domains can be achieved through DNS logs, network traffic analysis, and threat intelligence. The effectiveness hinges on the attacker's investment in the domain. A newly registered domain used for a quick phishing campaign is less painful to abandon than a long-standing domain used for persistent C2 operations.
For blue teams, monitoring newly registered domains (NRDs) and correlating domain reputation with observed network activity is a key strategy. The "pain" arises when an attacker has invested significant effort into a domain, making its loss a more substantial setback.
The Crucial Layer: Host Artifacts
This layer encompasses artifacts specific to a compromised host. These include registry keys, filenames, scheduled tasks, service names, mutexes, and specific configurations within the operating system or applications. Changing these requires a deeper understanding of the compromised environment and often involves more deliberate actions from the attacker.
For instance, a scheduled task named "SystemUpdateChecker" that executes malicious code is more difficult to change than a simple IP address. The attacker must not only remove the existing artifact but potentially find a new, less conspicuous way to achieve persistence or execute their payload. This requires more operational overhead and increases the risk of error.
Defenders can hunt for these artifacts by deep diving into system logs, memory analysis, and file system forensics. The effort required by the attacker to systematically remove or alter all such host-specific indicators means that detecting them can yield more enduring intelligence. This is where the defensive advantage begins to significantly outweigh the offensive agility.
The Apex: Adversary Tactics, Techniques, and Procedures (TTPs)
At the pinnacle of the Pyramid of Pain reside TTPs. These are the battle-tested methods and strategic approaches an attacker employs. They represent the attacker's modus operandi – how they gain initial access, escalate privileges, move laterally, exfiltrate data, and maintain persistence. TTPs are abstract concepts, representing strategic decisions rather than specific, easily changeable technical artifacts.
"Knowing *how* they operate is the ultimate intelligence. It’s the blueprint of their mind."
Changing TTPs requires an attacker to fundamentally alter their strategy, which is exceptionally difficult and disruptive. If an attacker consistently uses PowerShell for lateral movement, detecting and blocking that behavior forces them to re-evaluate their entire approach, potentially requiring new tools, scripts, or even a shift in their preferred attack vectors. This is the highest level of "pain" an adversary can experience.
Defenders who focus on identifying and mapping TTPs (often using frameworks like MITRE ATT&CK) gain the most strategic advantage. By understanding an adversary's patterns of behavior, organizations can build layered defenses that disrupt entire attack chains, not just individual indicators. This requires sophisticated threat hunting, behavioral analytics, and deep understanding of attacker methodologies.
Leveraging the Pyramid: Strategic Threat Hunting
The Pyramid of Pain is not just a theoretical construct; it's a practical guide for threat hunting and incident response. When an incident occurs, the IOCs discovered should be immediately mapped to their respective levels on the pyramid.
- Low-Level IOCs (Hashes, IPs, Domains): Use these for immediate blocking and containment. They are good for quick wins and cleaning up known malware. However, anticipate rapid evasion.
- Mid-Level IOCs (Host Artifacts): Investigate these further. They provide a clearer picture of persistence mechanisms and can inform searches for similar artifacts across the environment.
- High-Level IOCs (TTPs): These are gold. Understanding the TTPs allows the defender to build more robust, behavior-based detection rules and defensive strategies that anticipate future attacks, even if the specific IOCs change.
For example, if we detect a specific malware hash (Level 1), we immediately search for other systems exhibiting that hash. If we find it, we can block associated IPs and domains (Level 2/3). But the real value comes when we observe that the malware is using specific registry keys for persistence (Level 4) and a particular script for lateral movement (Level 5). This TTP-level intelligence allows us to hunt for *similar behaviors* across the entire network, proactively identifying and neutralizing threats before they fully manifest.
Veredicto del Ingeniero: Embracing Pain for Gain
The Pyramid of Pain is more than an academic exercise; it's a cornerstone of effective defensive strategy. Ignoring its hierarchy means treating all IOCs as equal, leading to wasted effort on fleeting indicators while potentially missing the attacker's core operational methods. For organizations serious about cybersecurity maturity, the objective must be to elevate detection capabilities to focus on the higher tiers of the pyramid. This requires investing in skilled threat hunters, advanced analytics platforms, and threat intelligence that goes beyond simple IOC feeds. The goal isn't just to find the crumbs an attacker leaves behind, but to understand their entire recipe, their operational playbook. By inflicting "pain" at the TTP level, defenders can truly disrupt adversaries and build resilient defenses.
Arsenal del Operador/Analista
- Threat Intelligence Platforms (TIPs): Tools like Anomali, ThreatConnect, or MISP to aggregate, analyze, and operationalize IOCs and TTPs from various sources.
- Endpoint Detection and Response (EDR) Solutions: Solutions like CrowdStrike, SentinelOne, or Microsoft Defender for Endpoint provide deep visibility into host activities, crucial for detecting host artifacts and behavioral anomalies.
- Security Information and Event Management (SIEM) Systems: Splunk, QRadar, or ELK Stack for aggregating and analyzing logs from various sources to detect patterns and TTPs.
- Network Traffic Analysis (NTA) Tools: Tools like Zeek (formerly Bro), Suricata, or commercial solutions to monitor network behavior for malicious communications.
- Malware Analysis Sandboxes: Cuckoo Sandbox, ANY.RUN, or VirusTotal for dynamic analysis of malware, revealing hashes, network activity, and behavioral artifacts.
- MITRE ATT&CK Framework: Not a tool, but an essential knowledge base and structure for understanding and mapping adversary TTPs.
- Books: "The Cuckoo's Egg" by Clifford Stoll (for historical context and the hunt), "Applied Network Security Monitoring" by Chris Sanders and Jason Smith (for practical network defense and analysis).
Preguntas Frecuentes
Q1: ¿Es posible que un atacante cambie sus TTPs rápidamente?
A1: Si bien los TTPs son más difíciles de cambiar que los IOCs de bajo nivel, un atacante hábil o un grupo altamente organizado pueden adaptar sus tácticas. Sin embargo, esto requiere un esfuerzo estratégico considerable y a menudo se manifiesta en nuevas heurísticas o patrones de comportamiento que aún pueden ser detectados.
Q2: ¿Cómo se relacionan las herramientas de EDR con la Pirámide del Dolor?
A2: Las EDR son cruciales para la detección de capas medias y altas de la pirámide. Permiten observar artefactos del host (registros, tareas) y, lo que es más importante, detectar comportamientos y TTPs observando procesos, llamadas al sistema y la interconexión de actividades.
Q3: ¿Deberíamos ignorar los IOCs de bajo nivel como hashes y IPs?
A3: Absolutamente no. Son la primera línea de defensa y esenciales para la contención rápida de amenazas conocidas. La clave es entender su limitación y no detenerse ahí, sino usarlos como punto de partida para ascender en la pirámide e identificar los TTPs subyacentes.
Q4: ¿Qué es lo más importante que un defensor puede aprender de la Pirámide del Dolor?
A4: La Pirámide del Dolor enseña que la inteligencia de amenazas más valiosa y duradera se centra en el comportamiento y la estrategia del adversario (TTPs), no solo en los artefactos técnicos que dejan atrás. Priorizar la detección de TTPs construye defensas más resilientes.
El Contrato: Fortificando el Perímetro Contra Ataques Sofisticados
Tu misión, si decides aceptarla, es la siguiente:
- Selecciona un informe de inteligencia de amenazas reciente (publicado en los últimos 3 meses) de una fuente reputada (ej. CISA, Mandiant, Recorded Future).
- Analiza los IOCs mencionados en el informe y clasifica al menos 5 de ellos en los niveles de la Pirámide del Dolor (Hash Value, IP Address, Domain Name, Host Artifact, TTP).
- Para cada IOC clasificado, describe brevemente el nivel de "dolor" que infligiría a un atacante si es detectado y cómo un atacante podría evadir esa detección específica.
- Propón una estrategia de defensa basada en TTPs que podría mitigar el impacto de las tácticas generales descritas en el informe, independientemente de los IOCs específicos.
Documenta tu análisis y compártelo en los comentarios. Demuestra que entiendes la diferencia entre apagar un fuego individual y desmantelar la estrategia incendiaria.

No comments:
Post a Comment