The digital realm is a battlefield. Every keystroke, every connection, a potential entry point. In this dark, intricate circus of code and data, understanding the adversary's tools is paramount for those who stand on the ramparts. Today, we're not just looking at Kali Linux; we're dissecting its capabilities, specifically its formidable password cracking utilities, not to break systems, but to understand their anatomy and build impregnable defenses.
This exposé is for the guardians, the blue teamers, the meticulous analysts who understand that the best defense is forged from a deep comprehension of the offense. We will peel back the layers of password cracking, revealing the methods, the tools, and, most importantly, the strategies to counter them. Consider this your tactical briefing from the heart of Sectemple.
Table of Contents
- The Silent Threat: Password Weaknesses
- Anatomy of a Password Crack: Methods and Machinery
- Kali Linux: The Cracker's Toolkit (and Your Defensive Counterparts)
- Fortifying the Gates: Defensive Strategies Against Password Attacks
- Engineer's Verdict: Beyond the Tool, Towards True Security
- Frequently Asked Questions
- The Contract: Your First Defensive Audit
The Silent Threat: Password Weaknesses
Passwords. They are the digital keys to our kingdoms, the first line of defense. Yet, they are often the weakest link, a fragile barrier easily shattered by those who know where to look. The proliferation of weak, reused, or easily guessable passwords is an open invitation to compromise. This isn't about malice; it's about fundamental security hygiene that is all too often neglected.
"A password is like a toothbrush. Don't share it, and change it regularly." - Many Security Experts, None of Whom Are Heard Enough.
Attackers exploit this human tendency for convenience. They understand that brute force, while computationally intensive, is often a matter of patience and resources. Dictionary attacks, hybrid approaches, and credential stuffing are not theoretical concepts; they are the bread and butter of many cyber intrusions.
Anatomy of a Password Crack: Methods and Machinery
Password cracking is an art form for the offensive, a stark lesson for the defensive. It's about exploiting the difference between complex, truly random strings and the patterns humans inevitably introduce. Let's break down the primary methodologies:
1. Dictionary Attacks: The Power of Common Words
This attack uses a predefined list of words and permutations (a "dictionary") to guess passwords. If a user's password is "password123" or "iloveyou", a simple dictionary attack will likely succeed rapidly. The effectiveness hinges on the quality and size of the dictionary used.
2. Brute-Force Attacks: The Relentless Assault
This is the most straightforward, albeit often the slowest, method. It involves systematically trying every possible combination of letters, numbers, and symbols. The time it takes is directly proportional to the password's length and complexity. For strong passwords (e.g., 12+ characters with mixed cases, numbers, and symbols), this can be computationally infeasible within practical timeframes.
3. Hybrid Attacks: The Best of Both Worlds
Combining dictionary and brute-force techniques. It starts with dictionary words and then applies rules (e.g., appending numbers, substituting characters like 'a' with '@') to create more sophisticated guesses. This is a common and effective strategy against moderately complex passwords.
4. Rule-Based Attacks: Mimicking Human Habits
Attackers analyze common password patterns and create rules to generate variations. This includes common substitutions (e.g., 'i' to '!', 's' to '$'), appending birth years, or using common keyboard sequences.
5. Credential Stuffing: The Repercussion of Reuse
This is where the danger of password reuse becomes critical. Attackers obtain leaked credentials from one breach and attempt to use them against other services. If a user has the same password for their email, banking, and social media, a single breach can compromise all accounts.
6. Rainbow Tables: Precomputed Shortcuts
These are precomputed tables of hash-to-password pairings. Instead of cracking each hash individually, attackers can use a rainbow table to quickly find the original password for a given hash. However, using "salts" (unique random data added to each password before hashing) makes rainbow tables significantly less effective.
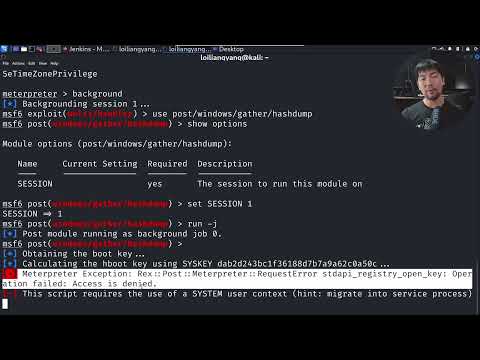
Kali Linux: The Cracker's Toolkit (and Your Defensive Counterparts)
Kali Linux is a distribution purpose-built for penetration testing and digital forensics. It comes pre-loaded with a vast array of tools, many of which are geared towards password auditing. Understanding these tools from a defensive perspective is crucial.
1. John the Ripper: The Classic
One of the oldest and most famous password cracking tools. It supports a wide range of hash types and modes of operation, including single-user, multi-user, and distributed cracking.
- Attack Vectors Exploited: Dictionary attacks, brute-force, hybrid attacks, rule-based attacks.
- Defensive Counterpart: Implement strong password policies, enforce length and complexity requirements, use salting with hashing algorithms, and monitor for repeated failed login attempts which might indicate John the Ripper in action.
2. Hashcat: The Modern Powerhouse
Widely regarded as the fastest and most advanced password recovery utility. Hashcat leverages the power of GPUs (Graphics Processing Units) for massive parallel processing, making it significantly faster than CPU-based tools for many hash types.
- Attack Vectors Exploited: All of the above, but significantly faster due to GPU acceleration.
- Defensive Counterpart: Strong password hashing with modern, computationally expensive algorithms (like Argon2, bcrypt, scrypt), proper salting, rate limiting on login attempts, and multi-factor authentication (MFA) are essential. Monitor system resource utilization for unusual spikes that might indicate brute-force attempts.
3. Hydra: Online Password Cracking
Hydra is a tool designed to attack network login services (like SSH, FTP, HTTP, SMB, RDP, etc.) by attempting to guess credentials. It's an online attack tool, meaning it works against live services.
- Attack Vectors Exploited: Brute-force and dictionary attacks against live network services.
- Defensive Counterpart: Implement account lockout policies after a certain number of failed login attempts. Use anomaly detection to spot an unusually high rate of failed logins to specific services. Employ MFA wherever possible, as it renders traditional password cracking useless for authentication.
4. Medusa: Another Network Login Cracker
Similar to Hydra, Medusa is a parallelized network login cracker that supports numerous protocols. It's designed for speed and flexibility.
- Attack Vectors Exploited: Brute-force and dictionary attacks against various network protocols.
- Defensive Counterpart: The same defenses as for Hydra: account lockout, suspicious login monitoring, and, critically, MFA. For protocols where MFA is not easily implementable, consider IP whitelisting or network segmentation to limit exposure.
Fortifying the Gates: Defensive Strategies Against Password Attacks
Knowing your enemy's arsenal is only half the battle. The real victory lies in building defenses that render those tools ineffective. Here’s how you lock down your digital fort:
1. Enforce Strong Password Policies
This is non-negotiable. Mandate minimum length (12-15 characters is a good baseline), complexity (uppercase, lowercase, numbers, symbols), and disallow common patterns or dictionary words. Regularly audit password policies to ensure they remain robust against evolving threats.
2. Implement Multi-Factor Authentication (MFA)
MFA is your most potent weapon. Even if an attacker obtains a user's password, they still need the second factor (e.g., a code from an authenticator app, a hardware token, a biometric scan) to gain access. Deploy it universally across all critical systems and services.
3. Utilize Modern Hashing Algorithms with Salting
When storing passwords (e.g., in a database), never store them in plain text. Use robust, modern hashing functions like Argon2, bcrypt, or scrypt. Crucially, always "salt" passwords. A salt is unique random data added to each password before hashing, making precomputed attacks like rainbow tables ineffective. Each user should have their own unique salt.
Consider this pseudocode for storing a password:
import hashlib
import os
def hash_password(password):
# Generate a unique salt for each password
salt = os.urandom(16) # 16 bytes of random data
# Hash the password using a strong algorithm (e.g., PBKDF2 with SHA256)
# Use a high iteration count for added security
hashed_password = hashlib.pbkdf2_hmac(
'sha256',
password.encode('utf-8'),
salt,
100000 # Number of iterations - adjust based on performance needs
)
# Store the salt and the hashed password together
return salt, hashed_password
def verify_password(stored_salt, stored_hashed_password, provided_password):
# Hash the provided password using the stored salt and same algorithm/iterations
hashed_provided_password = hashlib.pbkdf2_hmac(
'sha256',
provided_password.encode('utf-8'),
stored_salt,
100000
)
# Compare the hashes securely (constant-time comparison to prevent timing attacks)
return hashlib.compare_digest(stored_hashed_password, hashed_provided_password)
# Example Usage:
# user_password = input("Enter password: ")
# stored_salt, stored_hashed_password = hash_password(user_password)
# print(f"Stored Salt: {stored_salt.hex()}")
# print(f"Stored Hashed Password: {stored_hashed_password.hex()}")
# Verification step:
# login_attempt_password = input("Enter password again to verify: ")
# if verify_password(stored_salt, stored_hashed_password, login_attempt_password):
# print("Authentication successful!")
# else:
# print("Authentication failed.")
4. Implement Rate Limiting and Account Lockouts
Configure systems to temporarily lock accounts or introduce significant delays after a certain number of failed login attempts within a specified period. This drastically slows down brute-force and dictionary attacks, making them impractical.
5. Monitor Login Activity
Keep a close watch on authentication logs. Look for patterns like multiple failed logins from a single IP address, numerous login attempts on different accounts from one IP, or logins from unusual geographic locations. Security Information and Event Management (SIEM) systems are invaluable here.
6. Educate Your Users
The human element is crucial. Train users on the importance of strong, unique passwords. Educate them about phishing, social engineering, and the risks of password reuse. Regular security awareness training can significantly reduce the attack surface.
7. Regularly Audit and Patch Systems
Ensure all systems, especially authentication services, are up-to-date with the latest security patches. Vulnerabilities in authentication mechanisms can be directly exploited by attackers.
Engineer's Verdict: Beyond the Tool, Towards True Security
Kali Linux and tools like John the Ripper or Hashcat are powerful instruments. They are digital scalpels that can reveal critical vulnerabilities. However, the tool itself is neutral; its impact depends on the operator. As an engineer, I see these tools not as ends in themselves, but as means to an end: a more secure infrastructure.
Pros: Unparalleled insight into password security weaknesses, essential for proactive defense and penetration testing. These tools accelerate the discovery of vulnerabilities that could be exploited by malicious actors.
Cons: Can be misused to cause significant harm. Require a deep understanding of their implications and ethical boundaries. Relying solely on cracking tools without implementing robust defenses is a losing strategy.
Verdict: Absolutely indispensable for security professionals. For defenders, understanding them is as critical as understanding the threats they represent. Use them knowledgeably, ethically, and always with the goal of strengthening defenses. The true value isn't in breaking passwords, but in understanding how to prevent them from being broken.
Frequently Asked Questions
What is the most effective password cracking tool?
Hashcat is generally considered the most powerful due to its GPU acceleration. However, the "most effective" tool often depends on the specific target system, hash type, and available resources.
How can I prevent my password from being cracked?
Use long, complex, and unique passwords. Enable Multi-Factor Authentication (MFA) on all accounts. Avoid reusing passwords across different services. Keep your software updated.
Is using Kali Linux for password cracking illegal?
Using Kali Linux or any password cracking tool on systems or networks you do not have explicit, written permission to test is illegal and unethical. These tools are intended for legal penetration testing and security auditing purposes.
What is a "salt" in password security?
A salt is a unique, random piece of data that is added to a password before it is hashed. This ensures that even if two users have the same password, their stored hashes will be different, making precomputed attacks like rainbow tables ineffective.
Can MFA be cracked?
While MFA significantly increases security, it's not entirely infallible. Sophisticated attacks like SIM-swapping or man-in-the-middle attacks targeting the MFA prompt can sometimes bypass it. However, it remains one of the strongest forms of authentication available.
The Contract: Your First Defensive Audit
Your mission, should you choose to accept it, is to conduct a personal password security audit. For each of your critical online accounts (email, banking, main social media):
- Assess Current Password: If you recall it, evaluate its strength based on the criteria discussed (length, complexity, uniqueness).
- Check for Reuse: Determine if this password is used for any other service.
- Verify MFA Status: Confirm if MFA is enabled and correctly configured.
- Remediate: If your password is weak or reused, immediately change it to a strong, unique one and ensure MFA is active. If you don't have a password manager, consider researching one to manage your new, strong, unique passwords.

No comments:
Post a Comment