The digital realm is a battlefield. Every system, every byte of data, is a potential target. In this concrete jungle of code and networks, understanding the landscape – and more importantly, how to defend it – is paramount. Many are drawn to the siren song of cybersecurity, intrigued by the challenge, the intellectual sparring, and yes, the lucrative rewards. But the path isn't always clear. Where do you even begin when the enemy is invisible and the weapons are constantly evolving?
Today, we're not just looking at job titles; we're dissecting the operational roles that form the backbone of modern defense. Think of it as an intelligence briefing, outlining the key positions, the required skillsets, and the proven pathways to infiltrate these critical domains. Forget the Hollywood fantasy; this is about the gritty reality of incident response, vulnerability assessment, and threat containment. We'll map out the territory, identify the essential gear, and chart a course for those ready to answer the call.
The Pillars of Digital Defense: Key Cybersecurity Roles Exposed
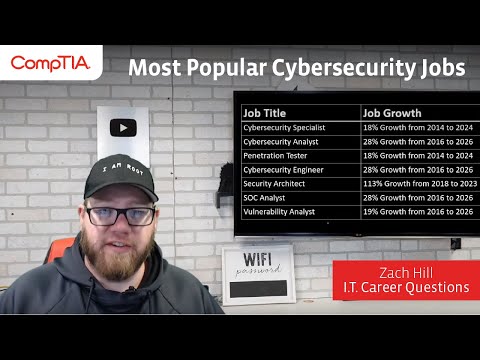
The cybersecurity industry is a sprawling ecosystem, but certain roles consistently emerge as critical infrastructure. These aren't just jobs; they are operational necessities for any entity that values its digital existence. Let's break down three of the most sought-after positions:
1. The Watchtower: Cybersecurity Analyst
Imagine a lone sentinel on a parapet, scanning the horizon for any sign of trouble. That's the essence of a Cybersecurity Analyst. These professionals are the first line of defense, tasked with monitoring networks, systems, and applications for security breaches or malicious activity. They sift through the constant stream of logs and alerts, differentiating between the mundane background noise and the subtle signals of an intrusion.
Their day-to-day involves:
- Analyzing security alerts and incidents.
- Investigating suspicious activities and identifying their source.
- Implementing and maintaining security measures.
- Developing security incident response plans.
- Staying abreast of the latest threat intelligence.
This role demands a keen eye for detail, strong analytical skills, and a deep understanding of network protocols, operating systems, and common attack vectors. It's a career path for those who thrive on problem-solving and information synthesis.
2. The Breacher: Penetration Tester (Ethical Hacker)
While analysts watch the perimeter, Penetration Testers actively test its integrity. These are the ethical hackers, hired to think like an adversary and exploit vulnerabilities before real attackers can. Their mission is to identify weaknesses in systems, applications, and networks through controlled simulated attacks.
A Penetration Tester's operational manual typically includes:
- Conducting reconnaissance and information gathering.
- Scanning for vulnerabilities using automated tools and manual techniques.
- Exploiting identified weaknesses to gain unauthorized access.
- Documenting findings and providing actionable recommendations for remediation.
- Reporting on the potential impact of discovered vulnerabilities.
This is where offensive security meets defensive strategy. It requires creativity, technical prowess across diverse technologies, and a solid understanding of exploit development and mitigation strategies. It’s the art of breaking in, legally, to make things stronger.
3. The Command Center: Security Operations Center (SOC) Analyst
The Security Operations Center is the nerve center of an organization's security posture. SOC Analysts are the operators within this hub, responsible for the continuous monitoring and analysis of security information from various sources. They are the ones receiving, triaging, and responding to security alerts, often working in shifts to ensure 24/7 protection.
Key responsibilities for a SOC Analyst include:
- Monitoring security dashboards and alerts from SIEM (Security Information and Event Management) systems.
- Performing initial investigations and classifying alerts based on severity.
- Escalating critical incidents to incident response teams.
- Contributing to the refinement of detection rules and playbooks.
- Ensuring compliance with security policies and procedures.
This role is crucial for immediate threat detection and response. It demands proficiency with security tools, a methodical approach, and the ability to remain calm and decisive under pressure.
The Blueprint to Entry: Acquiring Essential Skills and Certifications
Breaking into these roles isn't about luck; it's about preparation and strategic skill acquisition. The cybersecurity landscape is fiercely competitive, and employers look for concrete proof of competence. This is where targeted training and industry-recognized certifications become your most valuable assets. Think of them not as pieces of paper, but as validated tools in your operational arsenal.
Leveraging Training Programs
Formal IT training programs are the foundational bedrock. These provide the fundamental knowledge of networks, operating systems, and basic security principles that underpin all advanced cybersecurity disciplines. Whether through bootcamps, university courses, community college programs, or self-paced online platforms, building this core understanding is non-negotiable.
For example, a solid understanding of TCP/IP, DNS, HTTP/S, and common Windows and Linux administration tasks is essential before you can even begin to think about analyzing network traffic or configuring a firewall.
The Power of CompTIA Certifications
When discussing validated skills, the CompTIA suite of certifications frequently surfaces. These are vendor-neutral credentials that demonstrate a baseline proficiency recognized globally. For aspiring cybersecurity professionals, several CompTIA certifications are particularly relevant:
- CompTIA Security+: This is often the starting point. It covers foundational cybersecurity skills necessary for any cybersecurity role. It validates the ability to secure a network, manage risk, and respond to security incidents. For a Cybersecurity Analyst or SOC Analyst, this is often a prerequisite.
- CompTIA CySA+ (Cybersecurity Analyst+): As the name suggests, this certification is specifically geared towards the Cybersecurity Analyst role. It focuses on threat detection, analysis, and response, validating the skills needed to work within a SOC or as a dedicated analyst.
- CompTIA PenTest+: This certification is crucial for anyone looking to enter the Penetration Tester field. It covers the planning, scoping, and execution of penetration tests, including vulnerability assessment and reporting. It proves you understand the methodologies and tools required to ethically break into systems.
These certifications aren't just badges; they represent a structured learning path and a standardized measure of competency that hiring managers understand. Investing your time and resources into obtaining them can significantly shorten your job search and increase your earning potential. While you can learn many of these skills through self-study, a certification validates that knowledge to potential employers. For any serious pursuit, consider the pathways offered by CompTIA; they are widely respected and their credentials often open doors to entry-level and mid-level positions. For instance, acquiring the PenTest+ certification before applying for penetration testing roles is a strategic move that signals your seriousness and readiness.
The Analyst's Dossier: Navigating Your Path
So, how do you translate this knowledge into a career? It’s a process that requires persistence and a strategic mindset. The digital frontier is vast, and your journey into cybersecurity will be a continuous exploration.
"The only way to do great work is to love what you do." - Steve Jobs (often quoted in the context of finding your niche). In cybersecurity, finding roles that align with your innate curiosity and problem-solving drive is key to long-term success and resilience.
Start by acquiring the foundational IT skills. Then, focus on a specific area that sparks your interest—be it analysis, offensive testing, or operational defense. Pursue the relevant certifications that validate your expertise. Network with professionals in the field, attend industry events (even virtual ones), and contribute to open-source security projects if possible. Demonstrating initiative and a passion for the craft will set you apart.
Arsenal of the Operator/Analyst
- Essential Software: Kali Linux, Wireshark, Nmap, Metasploit Framework, Burp Suite (Community and Pro), John the Ripper, Aircrack-ng, Snort. For analysts, SIEM solutions like Splunk or ELK Stack (Elasticsearch, Logstash, Kibana) are vital.
- Hardware: A robust laptop capable of running virtual machines. For network testing, consider devices like the WiFi Pineapple (for educational purposes and authorized testing only).
- Key Reading: "The Web Application Hacker's Handbook," "Hacking: The Art of Exploitation," "Network Security Essentials," and CompTIA's official study guides for their certifications.
- Certifications to Target: CompTIA Security+, CySA+, PenTest+, EC-Council CEH, Offensive Security OSCP (for advanced pentesting).
- Online Labs and CTFs: Hack The Box, Try Hack Me, VulnHub, Immersive Labs. These are crucial for hands-on practice.
Remember, the cybersecurity job market is dynamic. Continuous learning isn't just a suggestion; it's a survival imperative. Threats evolve, tools change, and your knowledge must keep pace.
Frequently Asked Questions
What's the best entry-level cybersecurity job?
Typically, roles like IT Support Specialist with a security focus, Junior Security Analyst, or SOC Analyst Tier 1 are considered good entry points. Possessing certifications like CompTIA Security+ is highly beneficial.
How long does it take to get certified in cybersecurity?
It varies greatly depending on your existing IT knowledge and study habits. For foundational certifications like CompTIA Security+, many individuals can prepare and pass within 2-6 months of dedicated study.
Is cybersecurity a good career choice?
Absolutely. Demand for cybersecurity professionals is extremely high and projected to grow significantly. It offers challenging work, good compensation, and the opportunity to make a real impact.
Do I need a degree to get into cybersecurity?
While a degree can be helpful, it's often not strictly required, especially if you have relevant certifications, demonstrable skills through hands-on experience (like CTFs or home labs), and a strong portfolio.
What's the difference between a cybersecurity analyst and a SOC analyst?
While often overlapping, a Cybersecurity Analyst typically has a broader role in assessing and managing security risks across an organization. A SOC Analyst's role is more focused on the 24/7 monitoring, detection, and initial response to security incidents within a Security Operations Center.
The Contract: Secure Your Digital Future
The digital battlefield is constantly shifting. Understanding the roles of the Cybersecurity Analyst, Penetration Tester, and SOC Analyst is your first step in mapping this complex terrain. The path from novice to operative is paved with foundational knowledge, strategic skill acquisition, and validated expertise through certifications like CompTIA's offerings. It's not a sprint, but a marathon of continuous learning and adaptation.
Now, the onus is on you. Have you identified which role aligns with your operational aptitude? What are your first steps in acquiring the necessary skills and certifications? Share your strategy and any challenges you anticipate in the comments below. Let's build a collective intelligence report on navigating this critical field.

No comments:
Post a Comment